SIMULATION -
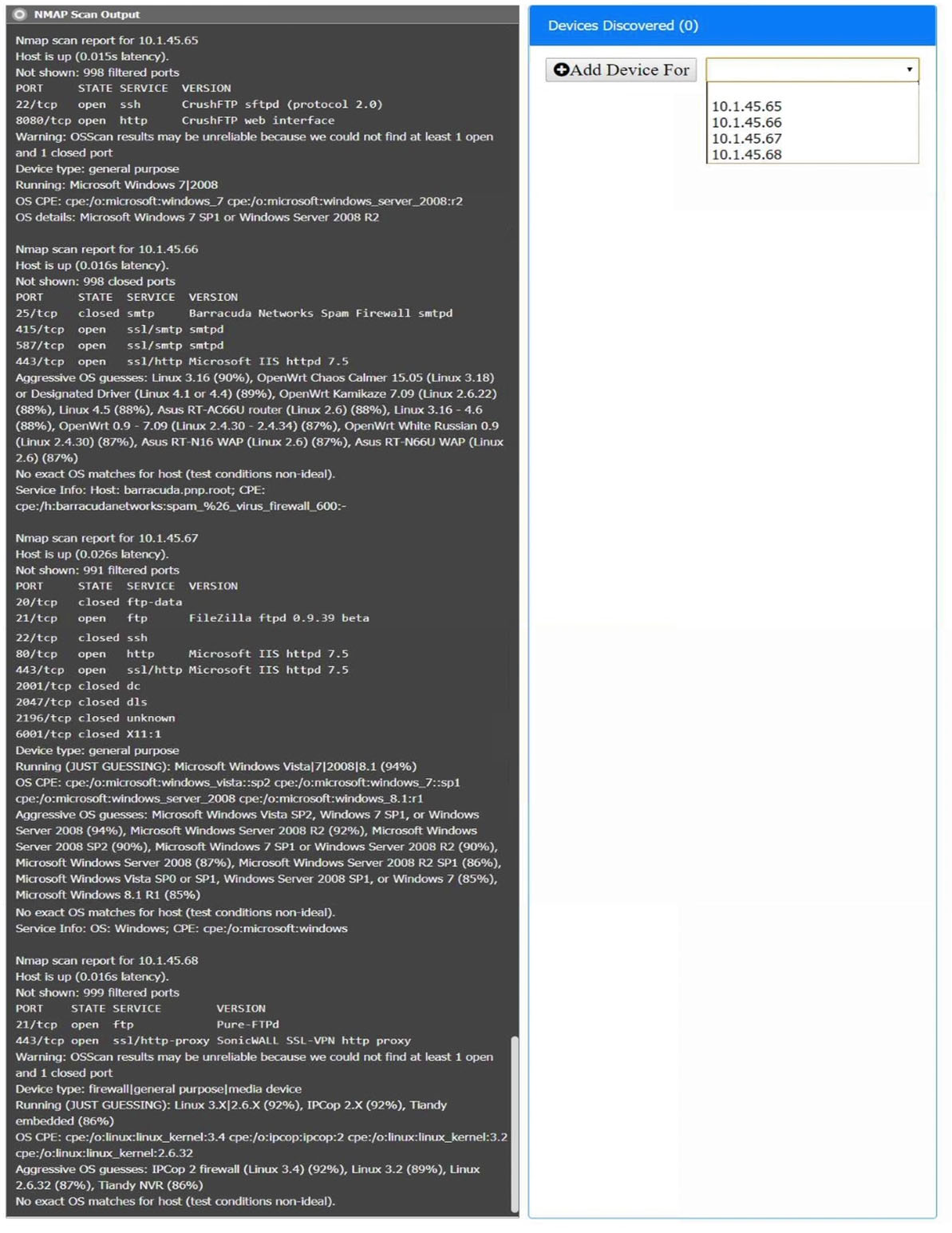
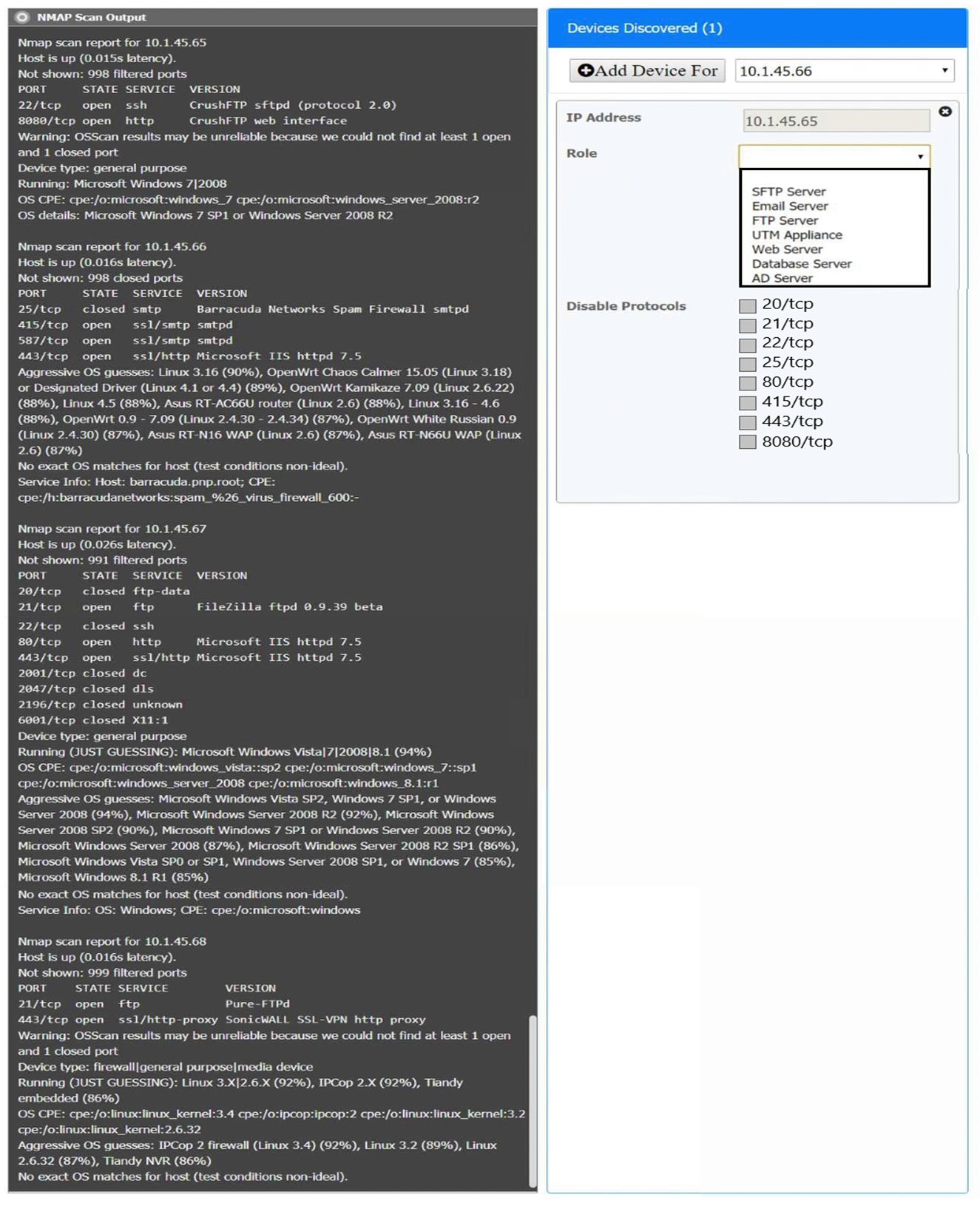
You are a security analyst tasked with interpreting an Nmap scan output from company's privileged network.
The company's hardening guidelines indicate the following:
✑ There should be one primary server or service per device.
✑ Only default ports should be used.
✑ Non-secure protocols should be disabled.
INSTRUCTIONS -
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
✑ The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)

✑ The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.