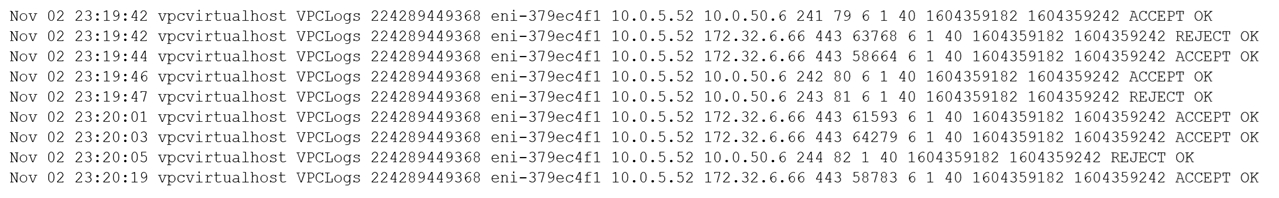
A security analyst observes the following while looking through network traffic in a company's cloud log:
Which of the following steps should the security analyst take FIRST?
A security analyst observes the following while looking through network traffic in a company's cloud log:

Which of the following steps should the security analyst take FIRST?
The network traffic logs suggest that the IP address 10.0.5.52 is scanning ports on the host 10.0.50.6. This kind of behavior, where multiple ports are being accessed in quick succession, is indicative of a port scan—a common reconnaissance activity that can be a precursor to an attack. The best immediate action is to quarantine the source of this suspicious activity, which is 10.0.5.52, to prevent any potential spread of malicious activity and then run a malware scan on it to identify any threats. This step prioritizes containment and further investigation to ensure the security of the network.
Answers C & D: These don't seem correct to me. Why would anyone want to isolate or investigate the destination IP 10.0.50.6 when the logs clearly show that the port scan is being sourced from 10.0.5.52? Option A: Isolating before checking what's going on seems too drastic . FIRST, I'd check what specific process(es) are triggering these connections via EDR portal. Thanks to embedded tools like Deep visibility, this should take less than 2 minutes. Sorry to differ with everybody on this one, but clearly option B for me.
I agree with this..
Part 1 of 2 Again, we have to pay attention to the key Word FIRST. what is the first thing you do? The First thing you do is investigate suspicious activities, so you need to figure out what the hell 10.0.50.6 is doing, which is clearly a port scan. after you determine there are suspicious activities from this Ip address based on the provided cloud log, then you can decide The next FIRST step Answer A is technically correct, but You can’t quarantine the entire Host 10.0.5.25 just because there is suspicious activity from on IP address, this will affect the availability of the host and we have no idea how big is that host is. Think of how big your containment is going to be if you isolate a whole host rather than just isolating the bad IP address. Answer B: checking EDR will give you an idea of what is connected to that host but depending on the size of the host this can take a long time and we already suspect 10.0.50.6 from the cloud log. So, this doesn’t help much as the moment.
part 2 of 2 Answer C isolate 10.0.50.6 is the correct answer because we know 10.0.50.6 is a private Ip and is doing port scans so we need to isolate it and further investigate. It could be that someone compromised that network or is a man-in-the-middle. Security groups will allow us to perform that isolation and keep the host running. This is the containment step which is the FIRST thing you do After identifying the incident in the Cloud log. Answer D is not correct because 10.0.50.6 is not doing any web activities, Therefore, a web log is useless in this case. 10.0.50.6 only scanned for ports: 241,242,243......
In this situation, the security analyst has observed network traffic from an IP address (10.0.5.52) that is attempting to access a host on the company's cloud (10.0.50.6) using a high number of connections. This behavior could potentially indicate a malware infection or a network attack, and it is important to take immediate action to prevent the attack from spreading or causing further harm. One of the first steps that the security analyst should take is to isolate the host (10.0.50.6) from the rest of the network using security groups. Security groups are a type of network security control that allow administrators to specify which incoming and outgoing traffic is allowed for a group of instances or resources. By isolating the host using security groups, the security analyst can prevent the attacker from gaining access to the host and potentially infecting other systems on the network. Option A, quarantining 10.0.5.52 and running a malware scan against the host, would not be the best step to take first as it does not address the issue of the attacker potentially gaining access to the host (10.0.50.6).
EDR should give the insight required really quickly. Analyst is just looking at logs, not responding to a malware alert so isolating systems and quarantining is too much action without an event. Threat hunting options would be C or D EDR is quicker and has data enrichment (web logs are brutal) OPTION B
It seems to me that 10.0.5.52 is doing a port scan of 10.0.50.6, as it is going port by port (241, 242, 243, 244). Hence, answer C.
Sorry, meant to say that the ANSWER IS A (disregard my previous comment pls).
The IP doing the port scan is 10.0.50.6, only 2 answers with that IP is C and D. D is the best answer since you look at the logs first to see what it was doing.
The incrementing destination port is indicative of a port scan. Since traffic is coming from an internal device, this could be a scheduled internal VA scan. Following NIST IR phases, we should first determine if this an either an incident or a false positive. B would be considered the Identification phase A would fall under containment. Source: currently work in a SOC is this is our procedure
A is the correct answer.
I agree with your answer, its A.
A is the best answer
This will help the analyst to determine if there are any malicious processes running on the host that are responsible for the network traffic. If there are, the analyst can then quarantine the host and run a malware scan against it. Option A could disrupt legitimate operations and should only be considered after initial investigation. Option C may be unnecessary if the connections are determined to be legitimate. And Option D will not help the analyst to determine if there are any malicious processes running on the host.
10.0.50.6 is doing a port scan, while other ips are using https (443). Best course of action is look at the logs related to that IP so D is the best answer
I was wrong, the increased attacks come from the ip 5.52 making A the best answer.
Answer is absolutely A
I think the answer is A
Ports 241-244 are reserved and and used for TCP/UDP. 10.0.5.52 to 10.0.50.6 could be communication from a user desktop to another host (printer, phone, video) on the internal network. I agree with answer B Access 10.0.5.52 via EDR and identify processes that have network connections to 172.32.6.66 using port 443.
The answer is A because 10.0.5.52 is almost certainly doing a port scan on 10.0.50.6. It is contacting the server on port 79, 80, 81, 82. It's sequential and this is not normal behavior, especially on these ports. It is almost certainly something malicious or out of the ordinary especially given some of the ports are blocked. The external IP it is reaching out to in between scan attempts could certainly be a C2 server. The first best step, giving the obvious strange behavior, is to quarantine the system doing the port scan.
This approach allows the security analyst to identify which processes are generating the traffic and potentially identify malicious activity. If malicious activity is found, subsequent steps would include containment (quarantining the host) and further investigation.