A CentOS computer was exploited during a penetration test. During initial reconnaissance, the penetration tester discovered that port 25 was open on an internal
Sendmail server. To remain stealthy, the tester ran the following command from the attack machine:
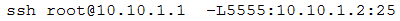
Which of the following would be the BEST command to use for further progress into the targeted network?