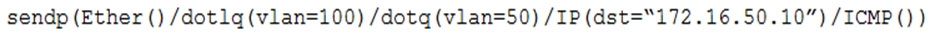Correct Answer: DThe penetration tester is attempting a double-tagging attack, a form of VLAN hopping. By sending a packet with two VLAN tags, the tester is trying to exploit the way some network switches handle VLAN tags. The outer tag (VLAN 100) is stripped by the first switch, leaving the inner tag (VLAN 50) intact, which can redirect the packet to a different VLAN (VLAN 50) than originally specified, potentially reaching a different network segment. This technique bypasses network segmentation and is used to gain access to network segments that are normally not accessible from the attacker's current VLAN.