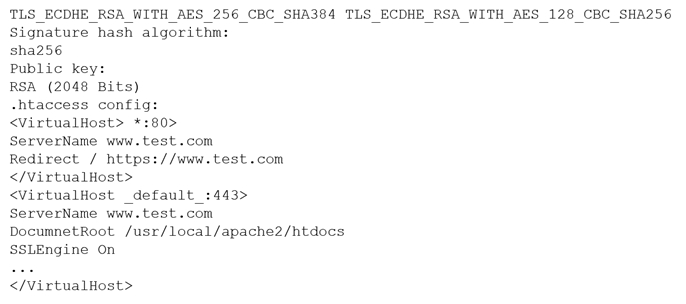
Also, due to "The decision on which cipher suite will be used depends on the web server. The agreed cipher suite is a combination of:
Key exchange algorithms, such as RSA, DH, ECDH, DHE, ECDHE, or PSK
Authentication/Digital Signature Algorithm, like RSA, ECDSA, or DSA
Bulk encryption algorithms, like AES, CHACHA20, Camellia, or ARIA
Message Authentication Code algorithms, such as SHA-256, and POLY1305"
https://www.keyfactor.com/blog/cipher-suites-explained/
Source:
Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)