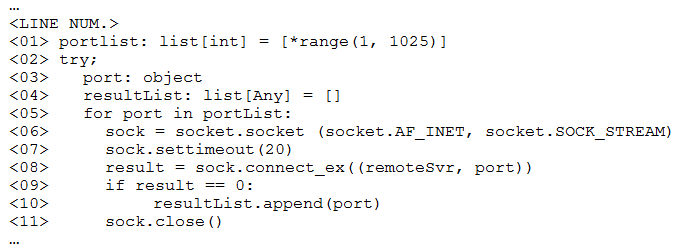
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code:
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code:

Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
The script triggers a 'probable port scan' alert in the IDS because it populates the portList with a range of ports from 1 to 1024 in numerical order using *range(1, 1025) on line 1. Scanning ports in sequential order is a common approach in port scanning, an activity often flagged by IDS systems as a security threat.
B is the only reasonable answer. A is in seconds not milliseconds. C Sock.STREAM = TCP DGRAM = UDP. Neither would indicate a port on its own.
A is wrong cause it's 20 seconds not milliseconds.
A - no, 20 seconds is fine socket.settimeout(value) Set a timeout on blocking socket operations. The value argument can be a nonnegative floating point number expressing seconds, or None. https://docs.python.org/3/library/socket.html#socket.socket.settimeout B - Port randomization is widely used in port scanners. By default, Nmap randomizes the scanned port order (except that certain commonly accessible ports are moved near the beginning for efficiency reasons) https://nmap.org/book/man-port-specification.html C - question is about triggering alert, not why it does not work D - same as C
B. \*range(1, 1025) on line 1 populated the portList list in numerical order. Populating the `portList` with a range of ports from 1 to 1024 in numerical order and then sequentially attempting connections to these ports is characteristic of a port scan. Intrusion Detection Systems (IDS) often detect port scans based on such sequential or numerous connection attempts within a short timeframe. This behavior is a common signature of port scanning activities, which is likely why the script triggered the alert.
The snippet of code is most likely to have triggered a "probable port scan" alert in the organization's IDS due to: B. *range(1, 1025) on line 1 populated the portList list in numerical order. The script is scanning a range of ports from 1 to 1024, which is the well-known range of ports. Scanning such a broad range of ports in numerical order is likely to be detected by an IDS as a probable port scan.