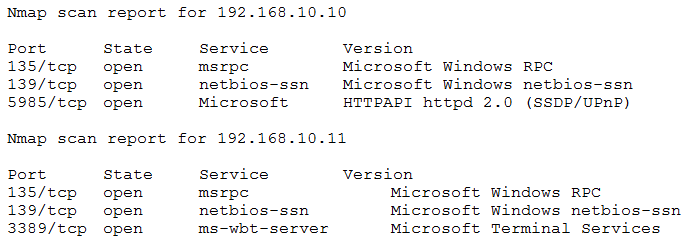
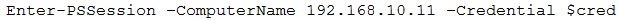Option A, "The tester input the incorrect IP address," is possible but less likely given that the Nmap scan results show that the target system is up and responding on the specified IP address.
Option B, "The command requires the -port 135 option," is incorrect since the command does not require a specific port to be specified.
Option D, "PowerShell requires administrative privilege," is not relevant to this issue since the command does not require administrative privilege. However, administrative privilege may be required to set up an RDP account on the target system.