The following line-numbered Python code snippet is being used in reconnaissance:
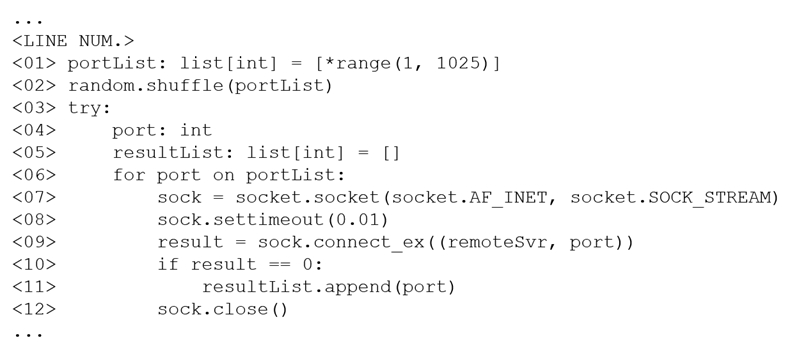
Which of the following line numbers from the script MOST likely contributed to the script triggering a `probable port scan` alert in the organization's IDS?
The following line-numbered Python code snippet is being used in reconnaissance:

Which of the following line numbers from the script MOST likely contributed to the script triggering a `probable port scan` alert in the organization's IDS?
Line 07 is the critical part of the script where the socket is created and set to use the TCP protocol, which is used to actively attempt connections to ports. This behavior of repeatedly creating sockets and attempting connections to various ports is characteristic of a port scanning activity and is likely to trigger an IDS alert for a probable port scan. While line 08 sets a short timeout which aids in rapid scanning, it is the actual connection attempts in line 07 that identify the script's action as port scanning.
I'd say D. 0.01 s is a super short and unusual setting for a timeout.
Based on the given script, the line number that most likely contributed to the script triggering a "probable port scan" alert in the organization's IDS is <08>: <08> sock.settimeout(0.01) The settimeout function sets the timeout value for a socket operation. In this case, the timeout is set to 0.01 seconds (10 milliseconds). A port scan typically involves attempting to connect to multiple ports on a target system to determine which ports are open or closed. Setting a low timeout value like 0.01 seconds suggests that the script is rapidly attempting connections to multiple ports in a short period. This behavior can trigger a "probable port scan" alert in an IDS (Intrusion Detection System) or firewall because it resembles the pattern of a port scanning activity. Port scanning is often associated with reconnaissance or probing of a network, which can be seen as a potential security threat. Therefore, the line <08> sock.settimeout(0.01) is most likely to have triggered the "probable port scan" alert in the IDS.
Yea I agree, set a T4 nmap scan and see what happens https://nmap.org/book/performance-timing-templates.html .01 seconds is 10 milliseconds - that is noisy
C. Line 07 The script is using a "portList" variable which is a list of integers, it is being shuffled by the command on line 2. The script then creates a socket on line 7 using the socket.socket() function and sets the socket to use the SOCK_STREAM protocol, which is used for TCP connections. This line (07) is the one that is likely to trigger a "probable port scan" alert on the organization's Intrusion Detection System (IDS) as the script is actively creating a TCP connection to each port specified in the "portList" variable, which is a behavior that is commonly associated with port scanning. Line 01 (A) is just defining the variable "portList" as a list of integers, it doesn't contribute to triggering an alert. Line 02 (B) is shuffling the "portList" variable, it doesn't contribute to triggering an alert either. Line 08 (D) is setting a timeout of 0.01 seconds for the socket, it doesn't contribute to triggering an alert. Line 12 (E) is closing the socket after the script finishes with it, it doesn't contribute to triggering an alert.
this answer maybe incorrect, dyor
D. The python script is setting the sock variable to pass socket.AF_INET and socket.SOCK_STREAM to the socket function in the socket class. The function isn’t called until line 9. This means that the timeout was the issue in line 8 which makes D the only correct answer and line 9 is where the function is actually called
time is set 0.01 which is very short and fast scan and will trigger IDS
I don't think that the variable that sets the parameters for the socket communication path causing it, because SOCK_STREAM is how you are connecting, yes TCP or UDP. IDS typically do packet inspection to find malicious code, methods, and abnormal traffic if the connection TCP or UDP there would be so much more flagging. So you can knock on any port you want at any time. Straight from their documentation socket.socket(family=AF_INET, type=SOCK_STREAM, proto=0, fileno=None) What this script is doing.
When try: fires off it's going to grab a random port from the range list. from there we need to define how we are going to communicate over this socket aka the "sock" we can use any of these socket.SOCK_STREAM socket.SOCK_DGRAM socket.SOCK_RAW socket.SOCK_RDM socket.SOCK_SEQPACKET socket.SOCK_CLOEXEC socket.SOCK_NONBLOCK Though everyone uses STREAM(TCP) or DGRAM(UDP) Next we are NOT going to use the default value "none" or kindly close our connection every 1-5 seconds after connecting to the port.
Instead, we are gonna hit each port or int value in that range variable "list." Then get data back and immediately close the port at 0.01 aka one-hundredth of a second. Times that by each port and in about 10 seconds you scanned 1024 ports that all timed out one-hundredth of a second if it was UDP I wouldn't doubt the IDS would still pick it up because you scanned 1024 ports in roughly 10 seconds as previously stated. That is noisy abnormal traffic. HOWEVER! We can always make it faster and even more noisier, but here we are not threading. This is only gonna go through one object in the range at a time, but we can absolutely thread it ;)
It's not a problem to connect to a port, it's rapidly connecting to one port after the other that's an issue.
Option C is the only answer that actively engages with the target network, all the other answers don't engage with the network whatsoever and only work with the code. I understand why there can be an argument made for D, but the only logic that makes sense to justify this answer is because line 07 is being triggered so frequently without enough time in between scans because the timeout in line 08 is so short; given the timeout period were longer it would make the scans seem less sketchy and less likely to alarm the IDS. But, the only way the IDS could alerted that there is an issue with rapid scans is if there is scanning in the first place, and line 07 is the sole reason the script scans, meaning option D must be the right answer.
Line 08 sets a timeout value for the socket, which limits the amount of time the script waits for a response from the remote server. While a short timeout value can be an indication of a port scan, by itself it is not sufficient to trigger an alert. A short timeout value could also be justified for legitimate reasons, such as reducing network latency. On the other hand, Line 07 is where the actual connection attempt is made for each port in the shuffled list. This behavior is more indicative of a port scan, as the script is attempting to connect to multiple ports in quick succession. This is a typical behavior of port scanning tools that are used to identify open ports on a remote system. Therefore, Line 07 is more likely to trigger a probable port scan alert in an IDS than Line 08.
The line most likely to trigger a probable port scan alert in the organization's IDS is Line 09. This line is responsible for attempting to connect to each port on the remote server, which is characteristic of port scanning behavior that IDS systems are designed to detect. Answer: C. Line 07
C Line 07: sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) • This line creates a new socket for each port in the portList. Creating multiple connections rapidly to various ports is a typical behavior of a port scan. IDS systems are designed to detect such patterns of behavior. Line 01: Initializes the list of ports from 1 to 1024. This defines the range of ports to be scanned but does not itself perform any actions. Line 02: Shuffles the port list to randomize the order of scanning. This helps in avoiding simple sequential scans but does not change the nature of the scan. Line 08: Sets a timeout for each connection attempt. While this might contribute to the rapid nature of the scan, it is not the primary action that would trigger an alert. Line 12: Closes the socket. Properly closing sockets is good practice, but it does not impact the detection of the scan significantly.
I would go with A. A: A list with more than 1000 ports is created which will be eventually looped through. Due to the eventual amount of incoming pings on different(!) ports the message "probable port scan" could be flagged. D: Sets a very short interval. So this potentially triggers a message in the IDS due to rapid connections. I agree that this could also be seen as correct, but just creating 1000 quick connections wouldn't necessarily result in a "probable port scan". e.g. if its always the same port... B: Only shuffles the port numbers. C: There is no connection to the remote/target. This only sets up the socket function, but does not connect. The actual connection is made in line 9
Very confusing question. Creating new TCP/IP sockets is a normal activity that happens when any network communication occurs, so this action alone wouldn’t necessarily trigger an alert. However, if a program creates sockets to try to connect to many different ports on a host in a short period of time, this could be seen as a port scanning activity
ChatGPT says line 7
Timeout is too short.
It's C, because it's the only command there that in any way interacts with the remote service. Without C), there would be nothing to detect.
Im going with A here simply because who scans port 1025?
In the given code snippet, line 07 contains the socket creation and connection attempt for each port in the portList. This behavior of iterating through a range of ports and attempting to establish a connection with each port is characteristic of a port scanning activity. Port scanning is often flagged as suspicious or potentially malicious behavior by intrusion detection systems (IDS) as it can be an indication of reconnaissance or attack preparation