A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
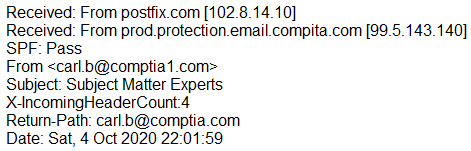
As part of the triage process, which of the following is the FIRST step the analyst should take?
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:

As part of the triage process, which of the following is the FIRST step the analyst should take?
The first step in the triage process should be to validate the final 'Received' header against the DNS entry of the domain. This helps to ensure that the email has been routed through the correct servers, and it can reveal whether the email is legitimate or fraudulent. While other steps like comparing the 'Return-Path' and 'Received' fields or blocking the email address might be necessary later, they are not the initial actions to take in the triage process.
The "Received" header is a field in the email header that shows the path the email has taken from the sender to the recipient. The DNS entry of the domain is a record in the Domain Name System (DNS) that specifies the server responsible for handling email for a particular domain. By comparing the "Received" header to the DNS entry, the analyst can determine whether the email has been routed through the correct servers and whether it is likely to be legitimate. Blocking the email address <a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="4e2d2f3c22602c0e2d21233e3a272f7f602d2123">[email protected]</a> (option A) may be necessary if the emails are confirmed to be spam, but it should not be the first step in the triage process. Validating the "Return-Path" and "Received" fields (option C) may be necessary as part of the triage process, but it is not the first step. Ignoring the emails because SPF validation is successful (option D) is not a recommended approach, as SPF validation alone is not sufficient to determine the legitimacy of an email.
Triage is the process of evaluating the findings and determining how to resolve them This clearly shows that the return path has been spoofed so the first thing you do is to compare the return path to the sender field. then you can block that Ip address.
You cannot compare the "Return-To" and the "Received" fields because the "Received" field does not contain a e-mail address.
Return-Path sorry.
Comparing the the return path to sender field would be irrelevant here as a first action because return paths are easily spoofed to replicate an authentic email. While this may reveal clues to help determine the authenticity of an email by using message headers it is not a reliable indicator. With the given information (the two sending servers, "received from") we are not dealing with an account compromise and blocking the end users email would not be fruitful, even temporarily.
B is the only legitimate, repeatable practice out of the options given.
B. Validate the final "Received" header against the DNS entry of the domain. The first step the analyst should take is to validate the authenticity of the emails. One way to do this is to check the final "Received" header, which is added by the mail server that received the message and indicates the IP address of the sender. The analyst should compare this header to the DNS (Domain Name System) entry for the domain listed in the header. If the IP address does not match the DNS entry, it is possible that the email is fraudulent or malicious.
I believe the first thing in triage is to validate, so that is why I am going with B
going with A, cause maybe there is BEC in this matter, i'm seeing different user with a different @comptia1 , might be just highjacked email
Have to make sure the sender is safe. Validate the IP has a DNS entry of an actual reputable website. Source: Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)
I think C is the best possible answer here. By looking at the return-path, I can see that a reply will go to a comptia.com and it was sent from an address from an IP using a comptia.com DNS entry. This is evidence that the email may be legitimate, or at least not spoofed. Combine that with the SPF pass and it begins to help determine how we should respond to these emails. If I saw the return-path was not a comptia.com email, I would immediately thing somebody is trying to use a compromised account to get information sent to a third-party.
There is some BEC in this email information that I didn't catch right away. I All caps the oddities in the first Received, it says "compita", which is not how it is supposed to be spelled. then the From email does not match the Return path email. "comptia1" vs "comptia". It seems there is some spoofing going on here. I vote B. See Below: Received: From postfix.com[102.8.14.10] Received: From prod.protection.email.COMPITA.com[99.5.143.140] SPF:Pass From<<a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="096a687b65276b494a4644595d404838276a6664">[email protected]</a>> Subject: Subject Matter Experts X-IncomingHeaderCount:4 Return-Path: <a href="/cdn-cgi/l/email-protection" class="__cf_email__" data-cfemail="d5b6b4a7b9fbb795969a9885819c94fbb6bab8">[email protected]</a> Date: Sat, 4 Oct 2020 22:01:59
C, from the list the most closed to determine a possible spam is C.
The 1st step should be identify if it's a threat.