SIMULATION -
An attack has occurred against a company.
INSTRUCTIONS -
You have been tasked to do the following:
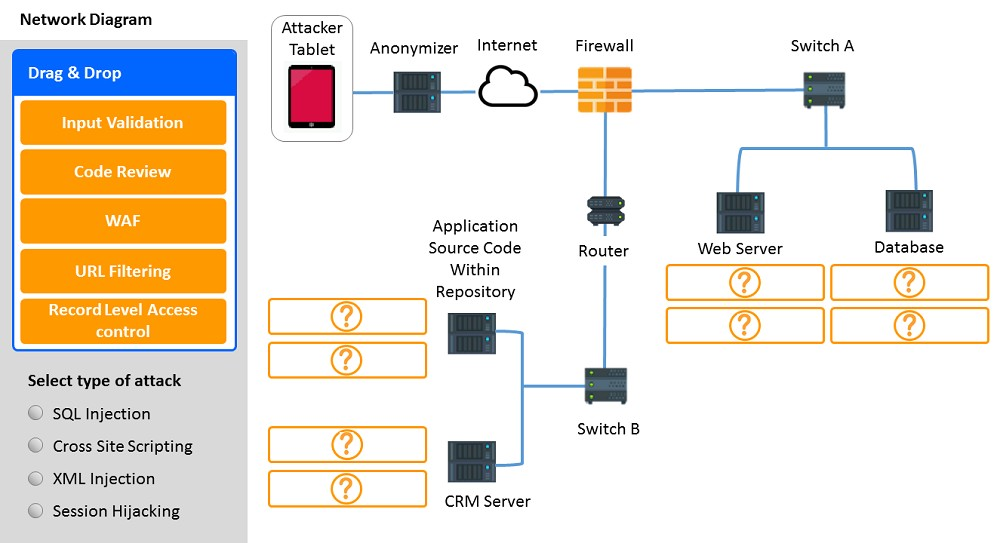
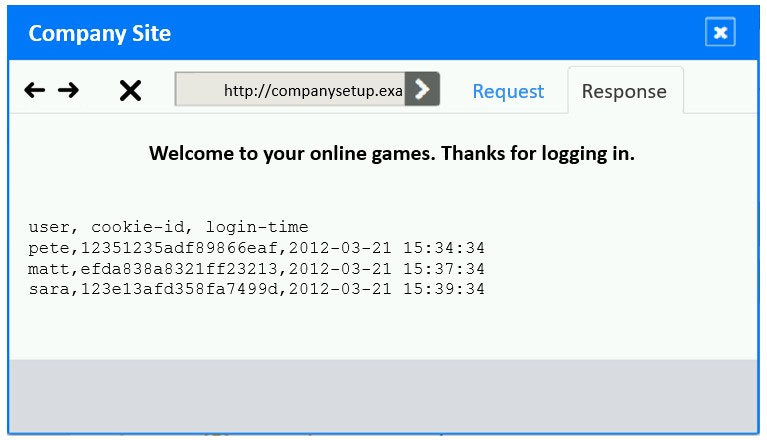
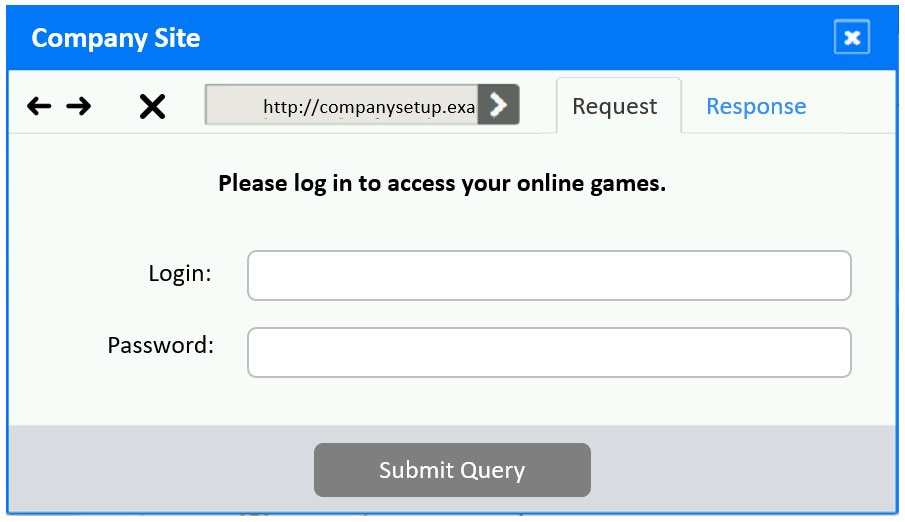
✑ Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output.
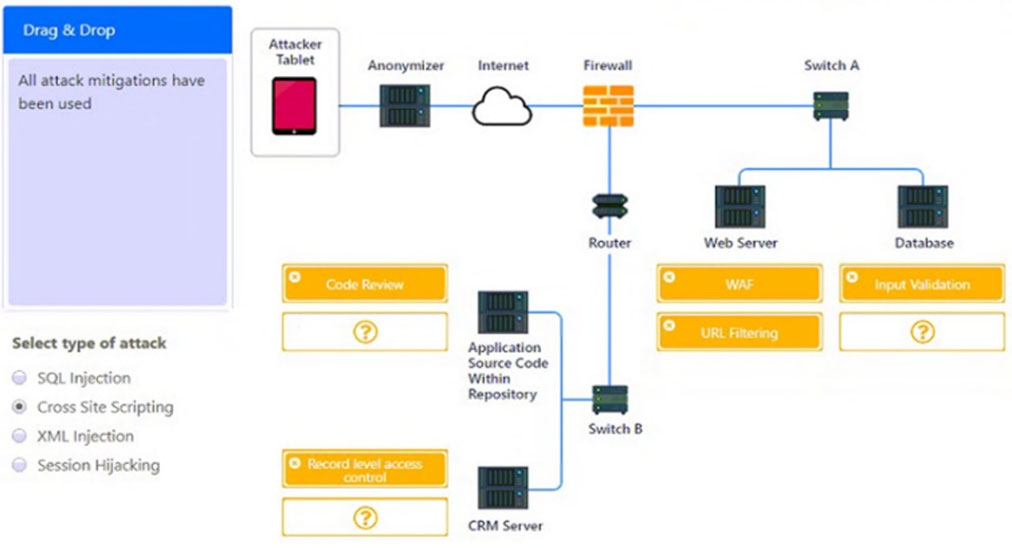
✑ Identify which compensating controls a developer should implement on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.