During an engagement, a penetration tester found the following list of strings inside a file:
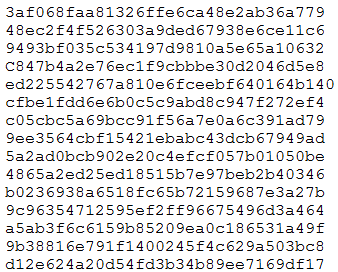
Which of the following is the BEST technique to determine the known plaintext of the strings?
During an engagement, a penetration tester found the following list of strings inside a file:

Which of the following is the BEST technique to determine the known plaintext of the strings?
The list of strings given in the file appears to be hash values. When dealing with hashed strings, one of the most efficient techniques to determine the original plaintext is to use a rainbow table attack. Rainbow tables are precomputed tables that map hash values to possible plaintexts, significantly reducing the time needed to perform the attack compared to brute-force methods. Unlike brute-force attacks, which try every possible combination, rainbow tables use precomputed hash values to quickly find a match, thus making the process more efficient. Therefore, a rainbow table attack is the best technique for determining the known plaintext of the hashed strings.
You use a rainbow table for hashes.
B - rainbow table since they're hashes.
**B. Rainbow table attack** A rainbow table attack is a method used to break hashed passwords by using precomputed tables of hash values for known plaintexts. This approach is more efficient than brute-force attacks as it significantly reduces the time needed to crack passwords by leveraging these precomputed tables. In this case, given the hashed strings, a rainbow table attack would be the best technique to determine the known plaintext.
the example shows 32 byte entries for all keys except one at 33 bytes. I would have said this was AES256 encryption... very tricky...
When dealing with hashed strings, and you want to determine the known plaintext of the strings, the BEST technique among the given options would likely be: B. Rainbow table attack A rainbow table is a precomputed table used for reversing cryptographic hash functions. Rainbow tables are used to crack password hashes by looking up the hash in the table and finding the corresponding plaintext value. It's often a more efficient way to discover the plaintext value of known hash functions compared to brute-force or dictionary attacks, especially if the hashes are not salted.