A security analyst is reviewing the following output:
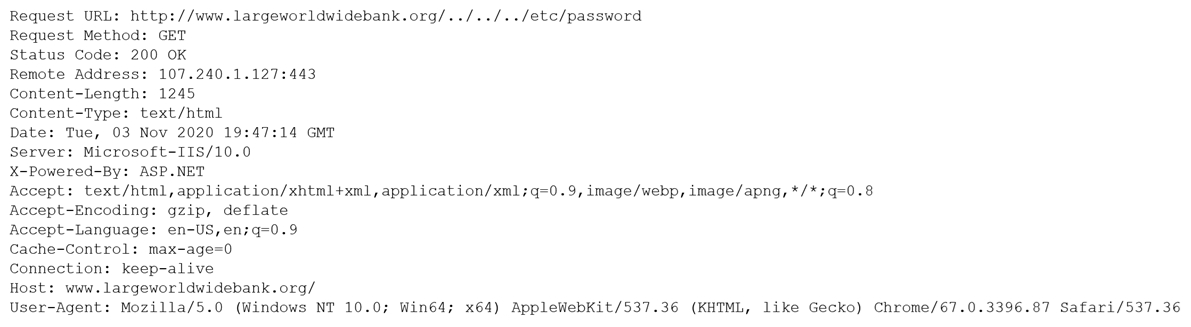
Which of the following would BEST mitigate this type of attack?
A security analyst is reviewing the following output:

Which of the following would BEST mitigate this type of attack?
The output indicates an attempt to access a sensitive file, such as "/etc/password", using a directory traversal attack. This attack type exploits insufficient validation of user-supplied input, specifically crafted URLs that access directories other than the intended one. Placing a Web Application Firewall (WAF) inline is the best mitigation strategy for such attacks. A WAF can inspect and filter HTTP traffic, blocking malicious requests aimed at exploiting vulnerabilities in the web application, thus protecting against directory traversal attacks.
The Answer is B
I agree. A WAF would be correct answer.
CASP #1 answer I keep seeing over and over... Place a WAF inline. Provide Input Validation to stop the bad guys from running exploits. Source: Verifying each answer against Chat GPT, my experience, other test banks, a written book, and weighing in the discussion from all users to create a 100% accurate guide for myself before I take the exam. (It isn't easy because of the time needed, but it is doing my diligence)
The answer must be B. It's a directory traversal attack.
I vote B, not because it eliminates LDAP injection issue (WAF can't do that, just make it harder to exploit the vulnerability in the application), but because all other answers make zero sense in this scenario. :)
Acunetix Website: The only way to effectively defend against directory traversal attacks is to carefully write the code of the website or web application and use user input sanitization libraries. Note that web application firewalls (WAF) do not eliminate directory traversal issues, just make it harder for the attacker to exploit vulnerabilities.
Answer: B. This (../../) is known as a traversal sequences and is considered a web application attack.
I agree I believe the answer is a WAF
B is correct
Attack is an XSS and the best solution is OWASP, best solution available is WAF
It's directory traversal hence the ../ but it is still B
I agree
Network Firewall does not make sense in this scenario. Best mitigation from those available is the WAF.
Traversal attack => WAF
The provided output indicates an attempt to access sensitive files on a web server, such as "/etc/password," which could be indicative of a directory traversal or path traversal attack. To best mitigate this type of attack, the most appropriate option is: B. Placing a WAF inline (Web Application Firewall) Explanation: Web Application Firewall (WAF): A WAF is designed to protect web applications from various attacks, including directory traversal. It can inspect and filter HTTP traffic between a web application and the Internet, blocking malicious requests that attempt to access unauthorized directories or files.
has anyone published a resource illustrating each type of attack with explanations. Where may I see examples of XSS attacks with explanations of how to distinguish different types of attacks from each other?
Need a WAF
A directory traversal vulnerability caused by specific character sequences within an improperly sanitized URL was identified in the VPN2S firewall. Zyxel has released a patch addressing directory traversal and command injection vulnerabilities in the VPN2S firewall.
The answer is definitely B. you need a web application firewall to prevent this. And from the log, we know is targeting the application layer.