Scenario: A Citrix Architect needs to design a new XenApp and XenDesktop environment for a bank. After the project kickoff meeting, the following business drivers have been identified and prioritized in the following order:
1. Increase security
2. Reduce costs
3. Improve the user experience
4. Simplify management
Later in the design process, the architect documents the design decisions shown in the Exhibit (only some are shown).
Click the Exhibit button to view the design decisions.
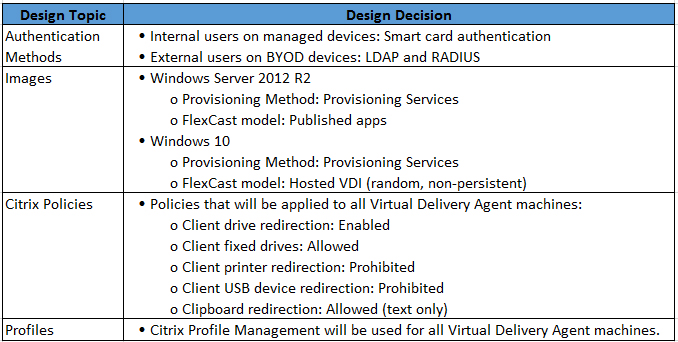
During the quality assurance review, the architect observes that one of these design decisions does NOT align with the business driver priorities.
Which design decision should be changed to match the prioritization of the business drivers?