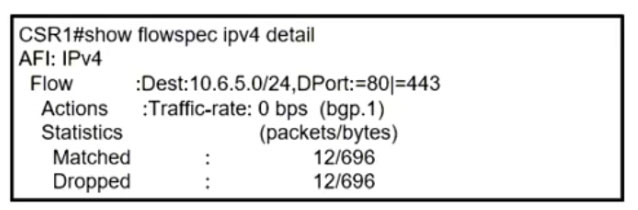
Refer to the exhibit. A network operator recently configured BGP FlowSpec for the internal IT network. What will be inferred from the configuration deployed on the network?

Refer to the exhibit. A network operator recently configured BGP FlowSpec for the internal IT network. What will be inferred from the configuration deployed on the network?
The configuration is learned via BGP FlowSpec, as indicated by the notation '(bgp.1)', which denotes a BGP-learned policy. The entries for 'matched' and 'dropped' packets (12 packets, 696 bytes each) show that there is currently active traffic being processed by this policy. Therefore, the correct choice is that the policy is learned via BGP FlowSpec and has active traffic.
C: (bgp.1) is displayed in the clients that receive policies from bgp flowspec https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/215637-configure-bgp-ipv6-flowspec.html
The difference between learned via BGP and locally configured https://www.noction.com/blog/ddos-mitigation
A sounds right then?
I go for D Why? Policy is learned via BGP Flowspec It has active traffic shown by the matches and drops The configuration does NOT drop ALL TCP ports 80 and 443 from what we see. It is only port 80 and 443 for destination 10.6.5.0/24, protocol number is missing for TCP/UDP. Anybody agree or disagree?
A and C excluded because it will drop TCP and UDP to 80 and 443 and destionation 10.6.5.0/24, so not "all traffic". D is right because we see 12/696 packets (active traffic) and it is learned via BGP (bgp.1)
I agree there is active traffic, but at the same time it doesn’t say “it will drop ONLY TCP 80 and 443” so C is still correct as it WILL drop TCP 80 and 443. So the wording is 100% correct. Damn Cisco!!!
I think this is a trick question where you don't pick the apparent obvious answer, it needs more checking. The output shows what was learned from the BGP flowspec policy and in there it tells us what is configured in the policy to match, what actions and the match/drops for any active traffic: Policy is configured for: Dest:10.6.5.0/24 Destination ports 80 and 443 Actions: traffic-rate: 0 bps So traffic matching the above will be dropped We see there is active traffic from Matched 12 and Dropped 12 packets But the policy is NOT configured to drop ALL traffic (ie to any destination) for TCP ports 80 and 443, only traffic for destination 10.6.5.0/24 and ports 80 and 443. It would include TCP and UDP as the protocol has not been configured for specific protocol 6 (TCP) or 17 (UDP) C is not correct for what we see configured. I still think D is correct because indeed this policy is learned via BGP Flowsec and does have active traffic on it as shows by the Matched and Dropped counters. https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2019/pdf/BRKSPG-3012.pdf
C because of the following reasons: 1: actions say (bgp.1) If it was locally configured it would actually list the name of the policy-map. 2: We can see that 12 packets were matched and 12 packets were droped, so it drops all traffic to those ports.
I guess so C is correct! I’m afraid that CSR1 is "flowspec client" on IOS-XE. https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_bgp/configuration/xe-16-6/irg-xe-16-6-book/C3PL-BGP-Flowspec-Client.html IOS XE software supports BGP flow specification client function and does not support BGP flow specification controller function. "flowspec server" must be IOS-XR. In this situation,"flowspec client" is advertised "flowspec-policy" by remote router(flowspec server) .
For a locally configured we see: RP/0/0/CPU0:P1#show flowspec ipv4 detail Fri Jul 12 02:05:45.266 UTC AFI: IPv4 Flow :Dest:88.88.88.88/32 Actions :Traffic-rate: 0 bps (policy.1.FLOWSPEC-PMAP.FLOWSPEC) For a BGP learnt wee see: PE1#show flowspec ipv4 detail AFI: IPv4 Flow :Dest:88.88.88.88/32 Actions :Traffic-rate: 0 bps (bgp.1) Statistics (packets/bytes) Matched : 0/0 Dropped : 0/0 Hence, answer is D. We are not dropping ALL traffic, only traffic for ports 80/443 to addresses 10.6.5.0/24
https://www.noction.com/blog/ddos-mitigation
Answer: A
"A" sound right according to this article: https://www.noction.com/blog/ddos-mitigation. nolbi published it on this thread before.
Option C is right. Cause it does not say it drops "ALL THE TRAFFIC", it says "it drops all the traffic "FOR" port TCP and UDP". Remember HTTP and HTTPS are TCP. Packets matched and dropped is just a counter, not necessarily means there is current active traffic passing by. So D is not right.
Match:12 Drop:12 The policy is learned via BGP --> "Actions:(bgp.1) FlowSpec and drops all traffic for TCP ports 80 and 443
I cannot agree because it will drop traffic to ports 80 and 443 AND destination 10.6.5.0/24, so not "all traffic".
Match:12 Drop:12 The policy is learned via BGP --> "Actions:(bgp.1) FlowSpec and drops all traffic for TCP ports 80 and 443
I cannot agree because it will drop traffic to ports 80 and 443 AND destination 10.6.5.0/24, so not "all traffic".
The correct answer is C. If it was locally configured, it would list the name of the policy-map tied to it. Showing (bgp.1) means that's configured on another node , and this one is the client. (just replicated this in GNS3)
I'd vote for D https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2019/pdf/BRKSPG-3012.pdf page 93 has a config demo
totally agree, the answer is C, This policy is learned via BGP FlowSpec.
https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/215637-configure-bgp-ipv6-flowspec.html