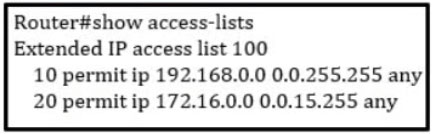
Refer to the exhibit. Which command set must be added to permit and log all traffic that comes from 172.20.10.1 in interface GigabitEthernet0/1 without impacting the functionality of the access list?
A.

B.

C.

D.
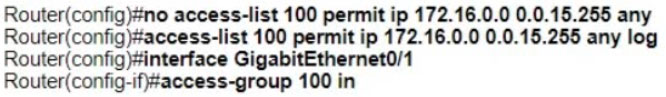

Refer to the exhibit. Which command set must be added to permit and log all traffic that comes from 172.20.10.1 in interface GigabitEthernet0/1 without impacting the functionality of the access list?
A.

B.

C.

D.

To permit and log all traffic from the IP address 172.20.10.1 on interface GigabitEthernet0/1 without altering the current ACL functionality, you should use the command set provided in option A. This method will add a new rule to the access list without disturbing the existing rules, as the IP address 172.20.10.1 does not overlap with the network 172.16.0.0/20 specified in the second rule. The commands are as follows: Router(config)#access-list 100 permit ip host 172.20.10.1 any log Router(config)#interface GigabitEthernet0/1 Router(config-if)#access-group 100 in.
A Two things to keep in mind. 1) the requirement of "WITHOUT impacting the functionality of the access list, and 2) the wildcard mask of ACE #20 does not overlap with the 172.20.10.1/32 therefore not affecting it Another thing to note is that without the sequence keyword, the new ACE is added at the end of the list.
very clear explanation.
A. tested again: cisco_R3#show access-lists 123 Extended IP access list 123 5 permit ip host 1.1.1.1 any log 15 permit ip host 4.4.4.0 any log cisco_R3#s runn | i 123 access-list 123 permit ip host 1.1.1.1 any log access-list 123 permit ip host 4.4.4.0 any log cisco_R3# cisco_R3#conf t Enter configuration commands, one per line. End with CNTL/Z. cisco_R3(config)#access-list 123 permit ip host 172.20.10.1 any log <<<<<<<<<<<<<<<<< cisco_R3(config)#^Z cisco_R3# cisco_R3#s runn | i 123 access-list 123 permit ip host 1.1.1.1 any log access-list 123 permit ip host 4.4.4.0 any log access-list 123 permit ip host 172.20.10.1 any log <<<<<<<<<<<<<< cisco_R3#show access-lists 123 Extended IP access list 123 5 permit ip host 1.1.1.1 any log 15 permit ip host 4.4.4.0 any log 25 permit ip host 172.20.10.1 any log <<<<<<<<<<<<<<<<<<<< cisco_R3#
A is correct. The syntax is wrong for B. You can't have everything on a single line. (config)#access-list 100 seq 5 % Unrecognized command Only if you use the syntax from A. C and D are not that specific so are out.
Disagree with you, if you don't indicate the exact position, it is added at the end of the ACL
For me, the C answer is the correct althouth I have to select a /24
The only problem with your answer is that you are permitting the entire network, the question wants you to just permit the Interface, not the entire network, that's how they got you
Go ahead and test before stating something please.
Mate, you can't have the entire syntax from B on a single line.
C is correct 100%
"...without impacting the functionality of the access list." IMO, once you add 5 you are changing the operation of the existing ACL.
Correct is answer C Answer A cannot be correct, as if the entry is added without sequence number is placed at the end, so its processed last. If its processed last then the same traffic will be matched earlier by 172.16.0.0. 0.0.15.255 statement and in result log will never be generated !! And question specifically ask for log ! Correct is answer C as correctly position new entry before 172.16.0.0. 0.0.15.255 statement thus enable logging, while not altering the rest of the ACL as the 172.20.10.0 0.0.0.255 would be matched by later statement and permitted.
look at the wildcard carefully. 172.16.0.0. 0.0.15.255 doesn't overlap with 172.20.10.0 0.0.0.255. Answer is A.
Not quite. The idea of a sequence number is to put the interesting traffic where you want it to be on the ACE. For example, if you have already permitted all traffic for a subnet and now wants to deny a single host from that subnet, then you will use sequence number to place it above the earlier permit statement, because ACL is processed from top-to-bottom. If you put the deny statement without a sequence number, it will append the ace at the bottom of the list, and it won't be effective for the purpose that you want to achieve. Therefore A is the correct answer because 172.20.10.1 is not overlapping with 172.16.0.0, and the list will be appended below. Chuckzero#sh ip access-lists Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any 30 deny ip host 172.20.10.1 any Chuckzero#
Answer A) is correct. As Clauster writes "the question wants you to just permit the Interface, not the entire network". That is why A is better than C.
A is correct 172.16.0.0 0.0.15.255 includes 172.16.0.0 - 172.16.15.255 Router(config)#do show access-list 100 Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any Router(config)#access-list 100 permit ip host 172.20.10.1 any log Router(config)#do show access-list 100 Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any 30 permit ip host 172.20.10.1 any log Router(config)#
A. extended ACL does not have seq keyword: Router(config)#access-list ? <1-99> IP standard access list <100-199> IP extended access list <1100-1199> Extended 48-bit MAC address access list <1300-1999> IP standard access list (expanded range) <200-299> Protocol type-code access list <2000-2699> IP extended access list (expanded range) <2700-2799> MPLS access list <300-399> DECnet access list <700-799> 48-bit MAC address access list compiled Enable IP access-list compilation dynamic-extended Extend the dynamic ACL absolute timer rate-limit Simple rate-limit specific access list Router(config)#access-list
extended NAMED ACL has seq: Router(config)#ip access-list extended MY_NAME ? <cr> Router(config)#ip access-list extended MY_NAME Router(config-ext-nacl)#? Ext Access List configuration commands: <1-2147483647> Sequence Number default Set a command to its defaults deny Specify packets to reject dynamic Specify a DYNAMIC list of PERMITs or DENYs evaluate Evaluate an access list exit Exit from access-list configuration mode no Negate a command or set its defaults permit Specify packets to forward remark Access list entry comment Router(config-ext-nacl)#
Router(config-ext-nacl)#3 permit udp any host 8.8.8.8 eq 53 log Router(config-ext-nacl)#do s access-l Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any 30 permit ip host 172.20.10.1 any log Extended IP access list MY_NAME 3 permit udp any host 8.8.8.8 eq domain log 10 deny ip any any log Router(config-ext-nacl)#
Router#show running-config | se Router#show running-config | section acc ip access-group 100 in ip access-list extended MY_NAME permit udp any host 8.8.8.8 eq domain log deny ip any any log access-list 100 permit ip 192.168.0.0 0.0.255.255 any access-list 100 permit ip 172.16.0.0 0.0.15.255 any access-list 100 permit ip host 172.20.10.1 any log Router#conf Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Router(config)#acc Router(config)#access-list 100 ? deny Specify packets to reject dynamic Specify a DYNAMIC list of PERMITs or DENYs permit Specify packets to forward remark Access list entry comment Router(config)#access-list 100
technically "C" also can be right ... Router(config)#ip access-list extended MY_NAME Router(config-ext-nacl)#5 permit tcp any host 8.8.8.8 eq 53 log Router(config-ext-nacl)#do s access-l Extended IP access list 100 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any 30 permit ip host 172.20.10.1 any log Extended IP access list MY_NAME 3 permit udp any host 8.8.8.8 eq domain log 5 permit tcp any host 8.8.8.8 eq domain log 10 deny ip any any log Router(config-ext-nacl)#
in the end my reply is - A Router(config)#ip access-list extended 100 Router(config-ext-nacl)# Router(config-ext-nacl)#5 permit ip host 1.1.1.1 any log Router(config-ext-nacl)# Router(config-ext-nacl)#do s access-l Extended IP access list 100 5 permit ip host 1.1.1.1 any log 10 permit ip 192.168.0.0 0.0.255.255 any 20 permit ip 172.16.0.0 0.0.15.255 any 30 permit ip host 172.20.10.1 any log 100 deny ip any any log Extended IP access list MY_NAME 3 permit udp any host 8.8.8.8 eq domain log 5 permit tcp any host 8.8.8.8 eq domain log 10 deny ip any any log Router(config-ext-nacl)#
Sorry. my answer is wrong. C is not correct. But A is correct.
A is correct
A is correct
..............................
Para mi la respuesta correcta es la C, la opción A nunca dejará log del host. La respuesta C si que lo hará
It is A because none of the existing ACEs match host 172.20.10.1. Even though this ACE would be the third in list, non of the other can match the host. B syntax is wrong (at least on the IOS I tried) C matches a whole subnet instead of a host D breaks the functionality of the ACL Correct answer: A
A is the correct answer. Been working with Cisco for a while I can just snipe correct syntax. idk what else to say.. Good luck folks. A is the correct answer.
People saying "B" do you have access to any network gear at all? or are you all book jockies? JFC. No wonder half the network admin pop sucks at their job, they have all these certs yet never touch a CLI LAB THIS STUFF BEFORE YOU COMMENT Answer is A
B is correct. There is no syntax error. without seq 5 there will be a match with 172.16.0.0/20
well there is. you can't have all that stuff on a single line.
172.16.0.0/20 range is 172.16.0.1 to 172.16.15.254