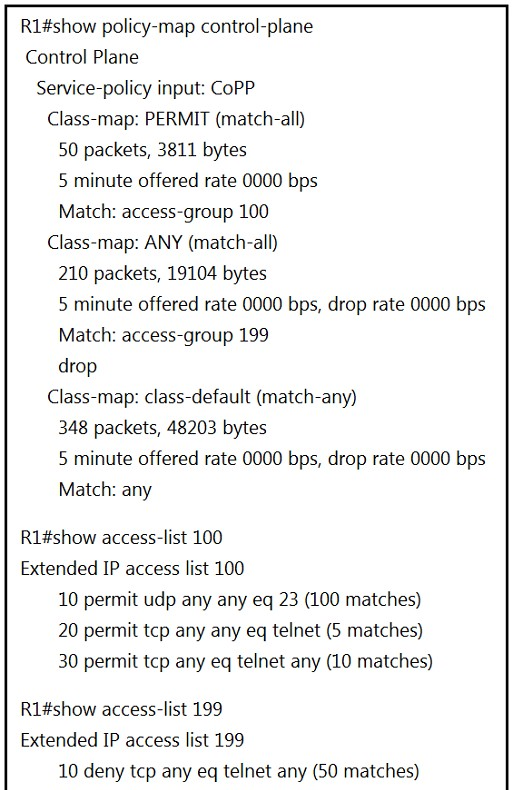
Refer to the exhibit. Which two actions restrict access to router R1 by SSH? (Choose two.)

Refer to the exhibit. Which two actions restrict access to router R1 by SSH? (Choose two.)
To restrict access to router R1 by SSH, removing class-map ANY from service-policy CoPP will prevent SSH traffic from being dropped by ACL 199, since class ANY currently matches and drops all traffic that hits access group 199. Configuring transport input ssh on line vty and removing sequence 30 from access list 100 will restrict incoming connections to SSH only, preventing Telnet access. This ensures that only SSH is used for management access to the router.
B and C. A is not correct - IMO
This image is cut off. Here's the is continuation below: R1# show access-list 199 Extended ip access list 199 10 deny tcp any eq telnet any (50 matches) 50 permit ip any any (1 match) R1# show running-config | section line vty line vty 0 4 login transport input telnet ssh transport output telnet ssh ------------------------------------------------------------------------- In order to restrict access to ssh only, shouldn't we limit the vty lines to transport ssh only? I believe the answer is B and C.
I have done that on lab, with the above output the SSH is not working! So i have remove Class-map ANY- then I was able to SSH to the router. So A is 100% ok. Other best option is C, since if we replace input telnet ssh to only SSH then you do not have access through telnet on the router.
A and C are right. A) ACL 199 match SSH traffic by sequence 50. The class-map match ACL 199 and this class is droping all traffic. if you remove the SSH traffic will match default class and will pass. If you don't permit SSH in ACL 100 it's mandatory remove this class. B) if you configure output ssh you are allowing R1 being the connection's client and i'm not sure if it is desided by the question. but you need to configure SSH input to ssh works and there is no option to do it except option C. C) It works with option A. Mandatory you need to input ssh in the lines vty to allow SSH and this is the unique option you can do it. We don't have the option to include SSH in ACL 100, so we need to remove the class ANY and input the SSH. Option C also removes sequence 30 in ACL 100 and this make the router unable to answer telnet connection. I would prefer to remover sequence 20, but removing sequence 30 also works. D) Does not make sense to me. E) does not make sense either.
Removing Sequence 30 in AC doesn't make the router unable to answer telnet connection. It is simply disallowing the remote device to respond back to the connection initiated by R1 because the control plane has the service policy applied in inbound direction. Hence Option B is not needed to be used to stop the outbound SSH connection thou the question never asked for this. Thou, your explanations for A and C being the right answers are correct.
I think this question is wrong as removing class ANY will mean you do not use CoPP at all. If the technology provides any benefits, why have questions that just allow all traffic? Anyway, i would not mind making a question like this wrong.
Class ANY = drop. It is dropping ip any any, means it is dropping SSH. We HAVE to remove it.
Class ANY = drop. It is dropping ip any any, means it is dropping SSH. We HAVE to remove it.
I think this question is wrong as removing class ANY will mean you do not use CoPP at all. If the technology provides any benefits, why have questions that just allow all traffic? Anyway, i would not mind making a question like this wrong.
Class ANY = drop. It is dropping ip any any, means it is dropping SSH. We HAVE to remove it.
Class ANY = drop. It is dropping ip any any, means it is dropping SSH. We HAVE to remove it.
A is correct. Note that once the ANY class-map is removed, SSH traffic will match the default class-map, which transmits all remaining traffic.
It seems that it is necessary to reduce the options for connecting to the router to SSH. Block telnet, allow SSH - it's clearer. Only the ANY captures(ACL199) SSH packets for policy(only this class-map can influence the ssh by control plane policy): 10 deny tcp any eq telnet any 50 permit ip any any <--------------------here(picture cropped) i.e. A By removing the ANY, we will skip the ssh packages default class. But apparently, "restrict" means that you need to disable telnet, leaving only ssh TO router. So we need the command "transport input ssh", i.e. C. P.S.: disgusting question
Full picture seen on the following site givin picture is wrong. https://www.actual4test.com/articles/dec-2021-pass-300-410-exam-in-first-attempt-updated300-410-actual4test-exam-question-q91-q113/
A. SSH traffic is matching line 50 of the class-map ANY and getting dropped. So class-map ANY needs to be removed to allow the SSH connection B. I believe this is for outbound connection, not relevant to the question. C. Correct.
A. SSH traffic is matching line 50 of the ACL 199 and getting dropped by class-map ANY. So class-map ANY needs to be removed to allow the SSH connection
“restrict access to router R1 by SSH“means only SSH can access the device,yes?
I don't see it having anything to do with blocking access via ssh.
I understood the meaning of the sentence, it means that ONLY SSH CAN CONNECT. A and C.
I think the following is easier. access list 100 40 permit tcp any any eq 22.
transport output ssh --- this will allow only ssh to be initiated from this device - which is not required - so A & C
can anyone explain this? i don't get it
The given answer is correct
B and C will force vty sessions to be SSH
B is transport out which is a outbound connection. No relevance to whats being asked.
B and C We only want SSH and no Telnet session. Configuring transport input/output ssh with remove the transport input telnet off the vty line. Also if you select B and C, you will also remove telnet from ACL 100.
Class ANY will match pretty much everything. The only thing it doesn't match is the outbound telnet from the router to where else (because the seq 10 in ACL 199 would match the return traffic). Therefore, you must remove this class because it would deny the inbound SSH traffic C would restrict inbound to be SSH only, despite that the "PERMIT" map would allow for inbound Telnet
AC is correct
A and C is the correct.
Not clear question, not sure if we are suppose to allow connection GOINGTO R1 via SSH or Allow R1 making SSH connection out only via SSH.
SSH is TCP 22. Where is TCP 22 permitted in this image?
Options are talking about Telnet when question is asking about SSH - so confused!
The given answer is correct
A answer is incorrect, if you remove de Class-map Any you are not dropping any traffic so you can still have access to the router via ssh. The correct answers are B, C.
Nope. The default class map permits the rest of the traffic.
Feels as if ACLs are not fully shown. They could have separated vty lines in one category and policy into another
Can anybody explain this question please?
B and C Some configuration output is missing, which is why some of you are choosing the wrong answers. See below for missing VTY Line config. line vty 0 4 transport input telnet ssh transport output telnet ssh We only want SSH and no Telnet session. Configuring transport input/output ssh with remove the transport input telnet off the vty line. Also if you select B and C, you will also remove telnet from ACL 100.
Awfully worded question....
A & C are correct B is incorrect, because; - there is no need for transport output statement, since we are talking about incommig traffic only. - sequence 20 in access list 100 is for outbound telnet, the question says restrict access TO the router by ssh (not from). here is the full exhibit R1#show policy-map control-plane Control Plane Service-policy input: CoPP Class-map: PERMIT (match-all) 50 packets, 3811 bytes 5 minute offered rate 0000 bps Match: access-group 100 Class-map: ANY (match-all) 210 packets, 19104 bytes 5 minute offered rate 0000 bps, drop rate 0000 bps Match: access-group 199 drop Class-map: class-default (match-any) 348 packets, 48203 bytes 5 minute offered rate 0000 bps, drop rate 0000 bps Match: any
R1#show access-list 100 Extended IP access list 100 10 permit udp any any eq 23 (100 matches) 20 permit tcp any any eq telnet (5 matches) 30 permit tcp any eq telnet any (10 matches) R1#show access-list 199 Extended IP access list 199 10 deny tcp any eq telnet any (50 matches) 50 permit ip any any (1 match) R1#show running-config | section line vty line vty 0 4 login transport input telnet ssh transport output telnet ssh