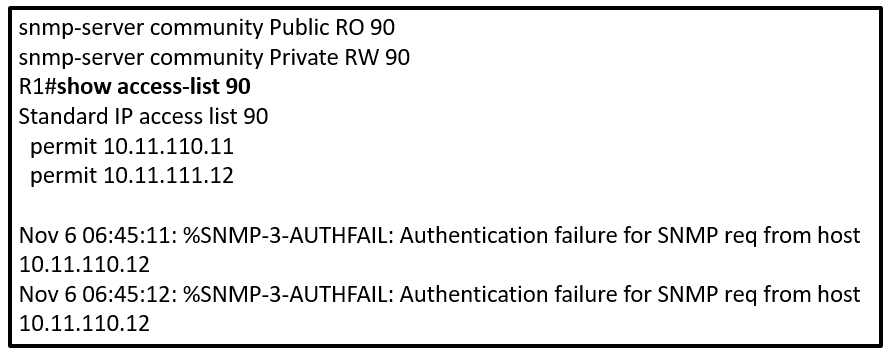
Lets think through this.
A) is wrong because SNMP functions in the management not the control plane.
B) this sounds correct, but if you think about it, it may cause unintended traffic denies. If we create a new ACL to deny the host, the answer does not specify other parameters, and we could assume that a permit any at the end will be configured as well.
C) is wrong, we are trying to block the host.
D) seems to be the best answer. If we use the same ACL 90, we are inherently deny any other hosts that do not require access to R1's management plane, and only permit the ones defined in the ACL.
D is the best answer
B works, but not entirely the best answer.