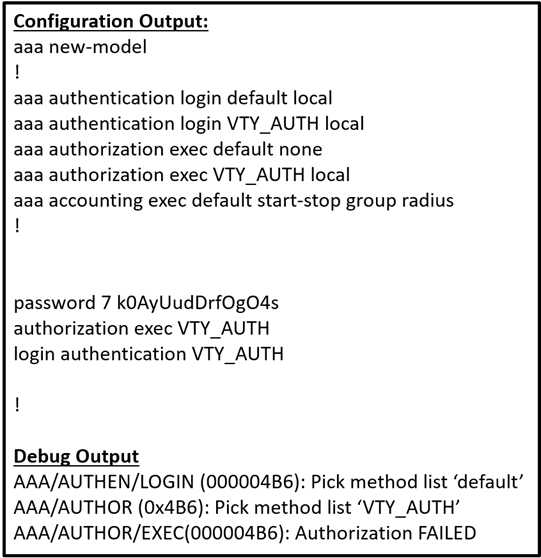
Refer to the exhibit.
Which action resolves the failed authentication attempt to the router?

Refer to the exhibit.
Which action resolves the failed authentication attempt to the router?
The debug output indicates that the authentication attempt failed for the VTY line, as it shows the login method list 'default' and the authorization method list 'VTY_AUTH' were picked. The failure occurs with 'authorization exec' using the 'VTY_AUTH' method list. Therefore, the correct resolution would be to configure the necessary authorization command on the VTY lines, making sure that the AAA authorization method list is properly applied. This is achieved by configuring 'aaa authorization exec' on the VTY lines, thus ensuring that authorization checks are correctly applied to incoming connections that use the VTY lines. Hence, configuring 'aaa authorization login command on line vty 0 4' is the correct action to resolve the failed authentication attempt to the router.
Debug says auth pick method was list default which implies that the user is connected to the console port. Of the answers listed only A would resolve the issue
if the default method is chosen, how does that imply the used is connected to the console port?
Agree A really does nothing to fix this issue. It is a bad question with missing config information needed to actually troubleshoot this. However, the only answer that is a command that can be configured is the one shown in answer A (aaa authorization console in global config mode), so only for that reason if I would pick A. (there are "aaa authentication login" commands, but no "aaa authorization login" commands, and even the "aaa authentication login" commands are done in global config, not on the lines.) at least not on the IOS's I have seen.
And yet if you read the full thread ( https://community.cisco.com/t5/network-access-control/console-authorization-issue/td-p/2492619 ), the solution was NOT A... A did nothing to fix the issue, in the end the whole AAA config on the system had to be reconfigured
Yeah, still all other options are completely wrong. A) at least makes sense.
"AAA authorization is disabled on the console by default. If AAA authorization is enabled on the console, disable it by configuring the no aaa authorization console command during the AAA configuration stage. AAA should be disabled on the console for user authentication."
Ref: Console authorization issue - Cisco Community Post by James Horne (12-17-2015 05:37 PM) What’s missing here is the aaa authorization console command. A. Configure aaa authorization console global command Correct answer. B. Configure aaa authorization console command on line vty 0 4 Wrong answer. C. Configure aaa authorization login command on line console 0 Wrong answer. D. Configure aaa authorization login command on line vty 0 4 Wrong answer.
option A: https://community.cisco.com/t5/network-access-control/console-authorization-issue/td-p/2492619
is "login authentication" in global configuration a valid command? I thought login authentication can only be applied to the console and vty lines. how does this question indicate that the someone is logging into the console? A is the only valid command (aaa is used to create method lists in global configuration)
A is correct