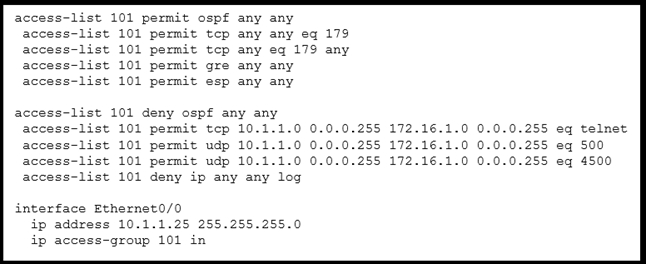
Refer to the exhibit. A network administrator has been tasked with securing VTY access to a router. Which access-list entry accomplishes this task?

Refer to the exhibit. A network administrator has been tasked with securing VTY access to a router. Which access-list entry accomplishes this task?
To secure VTY access to a router, Telnet and SSH are commonly used protocols. Among the options provided, only the 'eq telnet' parameter is valid for an access-list entry in Cisco configurations to permit Telnet traffic. Although SSH is more secure, the syntax 'eq ssh' is not valid; instead, port number 22 should be used to permit SSH. Since 'eq ssh' is not valid and is not part of the exhibit, the correct option would be to allow Telnet using 'eq telnet'. Therefore, the correct access-list entry is the one permitting TCP traffic on port 23 (Telnet).
there is no ssh entry in the table. I did not understand the answer.
Me neither
Remember: Among the keywords "eq ssh" does not exist, only "eq telnet". to configure ssh in the ACL we must use only its port number "eq 22". Answer correct is A.
in Pt no but in real life you can https://www.cisco.com/c/en/us/td/docs/app_ntwk_services/waas/waas/v431/command/reference/cmdref/ext_acl.html i vote for ssh
"A network administrator has been tasked with securing VTY access to a router". You need to secure VTY access and add SSH too, not just Telnet.
"Which access-list entry accomplishes this task" = Which of the lines does secure it. Telnet is trash, but is the only one configured on this access list.
But they said refer to the exhibit
By default, VTY lines allow remote access to a router without any restrictions, which can pose a security risk. However, by configuring and applying an access control list (ACL) to the VTY lines, you can control which IP addresses or networks are allowed or denied access to the router via Telnet or SSH. So, the ACL itself is a way of securing vty access, be it telnet or ssh. Since 'eq ssh' isn't a valid parameter, the answer should be A.
I hate these questions!!!!. A is correct because B, C, and D syntax is incorrect. There is no port labeled SCP, HTTPS, or SSH in the cisco command-line.
The issue with this question is that it's ambiguous as to whether it's asking us to identify an existing command in the configuration, or suggest an additional one. In the first case, the answer is obviously A. In the second case, it's obviously D. The problem is worsened by the fact that Telnet isn't a secure protocol, and allowing only Telnet access is arguably not "securing" anything, favoring SSH. So I chose D, but it could easily be A. Both are arguably correct.
Keyword SSH access: "live vty 0 15" configuration
eq ? <0-65535> Port number ftp File Transfer Protocol (21) pop3 Post Office Protocol v3 (110) smtp Simple Mail Transport Protocol (25) telnet Telnet (23) www World Wide Web (HTTP, 80)
Key word: Securing. With telnet you will not accomplish this requirement. Https and scp doesn't make sense here. So, I would go with D (ssh) even though the syntax is not fully correct.
eq ssh does not exist, you need to specify port 22
it´s A I have tested o a real router, SSH at the of the command is not acceptable, it must be eq 22 But telnet at the end of the command is acceptable.
The key point is securing vty access
I think the question is asking what command would you enter from the answers to enable a secure vty connection in which case its always ssh. telnet = not secure
According to the documentation below, actually there is a SSH keyword (C3 P7) https://www.cisco.com/c/en/us/td/docs/app_ntwk_services/waas/waas/v401_v403/command/reference/cmdref/ext_acl.pdf
I've noticed this is for Extended Access Lists, not standard ACL's. Google states: "A standard ACL allows or denies traffic access based on the source IP address, while an extended access control list can filter packets with a higher degree of specification. It can determine the types of traffic it allows or blocks beyond just the IP address to include TCP, ICMP, and UDP, for example." Maybe that's why SSH shows up as a CLI TCP Keyword.
Router(config)#access-list 101 permit tcp any 10.0.1.1 0.0.0.0 eq ssh ^ % Invalid input detected at '^' marker.
Going with D
The correct choice is D. The acces via telnet is already secured via eq telnet. Its posible to type telnet after eq on the extended acl (see pag. 50 CCNA 200-301 Official Cert Guide, Volume 2) then we only have to secure via ssh.
So I verified in GNS3 ACL's don't have SSH , you have to write port 22 in the command, that's why answer D is a trap and A is a valid answer.