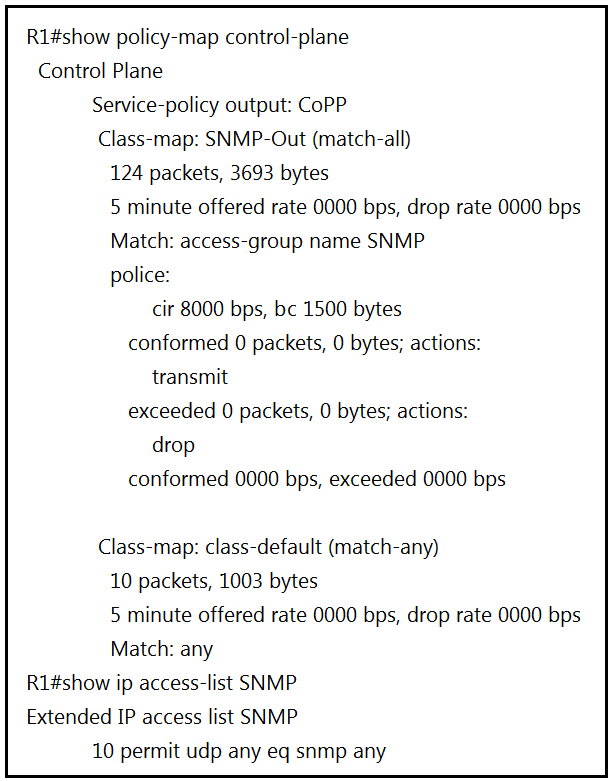
Refer to the exhibit. R1 is being monitored using SNMP and monitoring devices are getting only partial information.
What action should be taken to resolve this issue?

Refer to the exhibit. R1 is being monitored using SNMP and monitoring devices are getting only partial information.
What action should be taken to resolve this issue?
The access list currently allows only SNMP traffic (UDP port 161), but SNMP traps use UDP port 162. By modifying the access list to include snmptrap, we ensure that both SNMP queries and SNMP traps are permitted, which will result in more complete monitoring data. Therefore, including snmptrap in the access list is the appropriate action to resolve the issue.
The answer doesnt seem to be correct. D seems right. Anyone?
I think i upvoted you too soon, B seems like the better answer, tcp/ipv4 connectivity is already there. Just need to add in 162 I believe.
CoPP is applied inbound to protect your CPU from using to many cycles to process certain inbound management packets. The applied ACL on "10 permit udp any eq snmp any" is WRONG as it implies source port 161 to reach the actual router. This seems odd because the DESINATION port is actually 161 here and that one is listening on this actual router. To make the ACL actually match on inbound traffic hitting the SNMP server on this router, port 161 should be allowed as destination port as otherwise the management station cannot reach this router. Again, outbound traps should not be relavent for CoPP, if the traps overheat your CPU, it does not make a difference if they are blocked or not, the damage (high cpu) is already done. Summarazing here: the answer is D for sure as we need to allow inbound SNMP with having a destination port matching 161 == permit udep any any eq snmp (so the SNMP runs on the router, actually listening on that port) The management station is just a client in the dialog and generates a random source port.
B is the correct snmptrap uses port 161 snmp uses port 162 ip access-list extended ABC-ACL permit udp X.X.0.0 0.0.255.255 eq snmp host SERVER_IP !!source port is 161 permit udp X.X.0.0 0.0.255.255 host SERVER_IP eq snmptrap !!dest port is 162 https://community.cisco.com/t5/routing/acl-to-allow-snmp-traffic/td-p/1577251
1. Control-plane policing is only for the input direction. The question uses an "out" in the name to confuse us. The correct ACL to match SNMP poll would be in D. SNMP trap is the output direction and it is from the router to the monitoring server so it is not affected by the control-plane policing I would go with D
id say B. Just checked the IOS and came back with this: R5(config-ext-nacl)#permit udp host 2.2.2.2 eq ? snmp Simple Network Management Protocol (161) snmptrap SNMP Traps (162) It really appears to be B, because the scenario isnt referring to intermittent access, or access to the NMS being interrupted. Its just half the picture isnt available.
My opinion is C. Modify the CoPP policy to increase the configured CIR limit for SNMP. If you don't include the record to ACL the traffic will not be policed. so there is no reason to include Traps to the access list, and only SNMP ACL has action drop
Zeros on the counter. It seems there is no need to do something with the traffic limit. An unspecified destination address is basically the same as "any". Only part of the information comes to the server. Perhaps the snmp traps will complement it.
In my opinion, C is the correct one, note that if SNMP traps are not included in the SNMP ACL, the CoPP class-map SNMP-Out will be skipped for that traffic, but the "class-default" will match it and will forward the traffic without policying it. So the only viable answer is C.
B is correct. As the drop rate configured snmp is 0. Means that missing SNMP trap.
Device monitoring means collecting and analyzing the SNMP trap messages that devices send to the logging server. But ACL SNMP permits only SNMP traffic. This must be modified. A. Modify the CoPP policy to increase the configured exceeded limit for SNMP. Wrong answer. B. Modify the access list to include snmptrap. Correct answer. C. Modify the CoPP policy to increase the configured CIR limit for SNMP. Wrong answer. D. Modify the access list to add a second line to allow udp any any eq snmp. Wrong answer.
Hi, Can I have your email ID as I wanted to ask you something? Thanks.
acces-lsi permit : snmp and snmptraps (agent client). The option corret is B
B is the correct
The given answer is correct. B is the right answer
"10 permit udp eq snmp any " means that : Send out only snmp informaton provide from me to any destination(mainly the NMS_SERVER). If sth like TCP event occurs in the device( SNMP_Agent as an example) is not gonna be sent to the NMS; This one is going to see only everything about UDP from the Agent . In this case to get all information provide by the Agent (R1) we need to configure snmp_trap on it....
My apologizes... After reading the question more carefully, I would go with C. The ACL is correct. The PM is applied for outbound. So the ACL would match the response traffic from this router to the SNMP server. The class-default already matches everything so even though it is an SNMP trap, it would fall in that category and will pass. Increasing the exceed limit doesn't help because its action is to drop anyway.
D There are no matches for the traffic, so has to be related to ACL. This leaves us with B or D. The questions indicates they're getting some info and it looks like responses to SNMP requests are allowed through ACL/COPP Policy. Seems like this would just leave SNMP Traps that aren't getting out then.
The correct answer is D. The access-list is wrong, the first part of ACL is source and not destination port.
B is the correct snmp = UDP port 161 snmptrap = UDP port 162