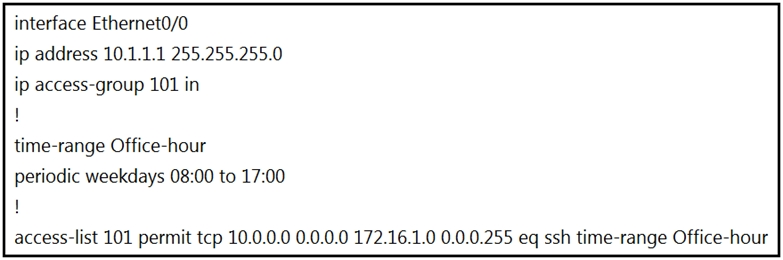
Refer to the exhibit. An IT staff member comes into the office during normal office hours and cannot access devices through SSH.
Which action should be taken to resolve this issue?

Refer to the exhibit. An IT staff member comes into the office during normal office hours and cannot access devices through SSH.
Which action should be taken to resolve this issue?
The correct approach is to modify the access list to use the correct IP address. The current access list is too restrictive as it allows SSH access only from the IP address 10.0.0.0, which is not valid in this context. Changing the IP to the IT staff member's IP address or a more appropriate range (e.g., 10.1.1.x) will resolve the issue, ensuring that SSH access is correctly granted during the specified time range. Adjusting the subnet mask is not necessary in this case, as it is more appropriate to directly correct the specific IP address the access list should permit.
I changed my mind, i think it is A. Because C says subnetmask. And i dont think they would use the word subnet mask instead of wildcard mask. For A to be true, we need to know that IT guy`s ip address and use that to correct the ACL
..the main problem is sender address 10.0.0.0 It's unlikely that our worker has such an address configured. And then we should choose honey A and C. A - if it is assumed that the employee works from a PС from the network 10.1.1.0/24, then changing the address to 10.1.1.x/32 is reasonable. C - let's say we set /8. It's not very elegant, but any package from 10.1.1.0/24 will pass this access list. It seems to me that opting for a stricter rule is more correct than giving access to the entire 10/8 network.
I believed (A) is correct answer, below is the intended config: access-list 101 permit tcp 10.1.1.1 0.0.0.0 172.16.1.0 0.0.0.255 eq ssh time-range Office-hour
The source 10.0.0.0 0.0.0.0 means host 10.0.0.0, and it is not valid for this topology. So, we need to correct the source ip address for sure.
The information is missing, what should we set as the source in the ACL. Is the device shown in the question the source or the destination of the telnet traffic? Or is telnet transiting through it? If it is the source, and telnet should be initiated from this device (10.1.1.1 0.0.0.0) to other devices (172.16.1.0 0.0.0.255), then: -the ACL won't work. We can't apply any ACL to the outbound traffic generated locally by the router itself If telnet is transiting through this device (for instance, coming from a LAN connected to E0/0), then: -we should correct the ip address and wildcard mask, too: access-list 101 permit tcp 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255 eq ssh time-range Office-hour The device with IP 10.1.1.1 could also be the destination, and telnet traffic would enter on E0/0 inbound. In that case the ACL would be something like this: access-list 101 permit tcp 172.16.1.0 0.0.0.255 host 10.1.1.1 eq ssh time-range Office-hour The output does not show clearly, how they want to use the ACL.
*I meant SSH traffic.
I like A, more
On a router, access-list 101 permits SSH connections from 10.0.0.0/0.0.0.0, which equals to 10.0.0.0/255.255.255.255, which equals to 10.0.0.0/32. In other words, SSH access is allowed only to this IP address, and not to a subnet. The correct syntax could be: access-list 101 permit tcp 10.0.0.0 0.0.0.255 … But, since the question refers to a single IT staff member, the solution to the problem could be allowing SSH access only to a single IP address, like this: access-list 101 permit tcp 10.1.1.1 0.0.0.0 … A. Modify the access list to use the correct IP address. Correct answer. B. Configure the correct time range. Wrong answer. C. Modify the access list to correct the subnet mask. Wrong answer. D. Configure the access list in the outbound direction. Wrong answer.
I would chose "C", but the word "subnet mask" got me... "A" seems more right, but I am not sure.
Im going with A considering that 0.0.0.0 is the equivalent to 255.255.255.255 on on normal mask. So the likelihood of doing a mistake here (considering the scenario) its on the ip address.
if the question would suggest multiple IT staff members, I would go with C but its not the case.
This is such a BS question as you could change the IP address or subnet mask, which is really the wildcard. I be selecting A to change the IP and leave the wildcard to match all bits
The question didn't say what IP the connection is from or to. It didn't say the SSH is to the router itself. It is more than likely the SSH traffic is through the router instead of destined or sourced from the router. In that case, I think C would make more sense. 10.0.0.0/0.0.0.0 is clearly wrong.
A A is more accurate but you have to modify both IP and Wilcard 10.1.1.0 0.0.0.255 it should be like that
Okay, I will go with C. I was torn between A and C, but C seems more plausible as the answer because chainging the IP address of the source portion of the ACL will only apply to one host device, when there could be a Staff with multiple devices... I agree that there may be a discrepancy in wording of Subnet Mask and Wildcard mask, but subnetmask can be changed from 0.0.0.0 to 0.255.255.255 to cover the correct subnetmask.
My choice: Answer C Enough to change the ACL like this: access-list 101 permit tcp 10.0.0.0 0.1.255.255 172.16.1.0 0.0.0.255 eq ssh time-range Office-hour With answer A, we get only one IP address, from where ssh allowed, while this company has an IT staff.
permit 10.0.0.0 0.0.0.0 will only allow a host with 10.0.0.0 IP but subnet is the wrong word, should be mask.
The question is "An IT staff member ", in this case it is only 1 person, the correct answer is A. If the question were "IT staff members" the correct answer will be C
I agree that A is correct because ACL's use wildcard bits and the entry matches only the 10.0.0.0 address. Why is D not considered? If the someone is trying to access remote devices wouldn't the ACL need to be applied in the outbound direction?
it´s A the IT member´s IP address is 10.1.1.1 so we must modify the access list to match the ip address permit tcp 10.1.1.1 0.0.0.0