Refer to the exhibit. An IKEv2 site-to-site tunnel between an ASA and a remote peer is not building successfully. What will fix the problem based on the debug output?

Refer to the exhibit. An IKEv2 site-to-site tunnel between an ASA and a remote peer is not building successfully. What will fix the problem based on the debug output?
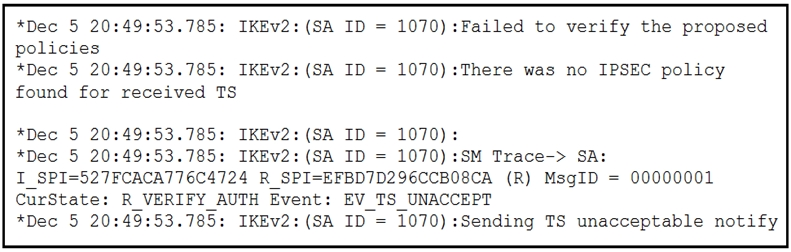
Based on the debug output, the error message indicates that there was no IPSEC policy found for the received Traffic Selector (TS). This suggests that the issue is related to the identification of the traffic to be tunneled, which is configured using crypto access lists (ACLs). Therefore, correcting the crypto access lists on both VPN devices to properly match the interesting traffic will resolve the issue.
TS - traffic selector - which traffic to be tunneled. TS_UNACCEPTABLE means the interesting traffic doesn't match
the error message says, "There was no IPSEC POLICY found for received TS" TS = Traffic selector (IP), so this means nothing to do with the IP but rather IPSec policy
C - need to modify ACLs
C - need to modify ACLs to properly identify interesting traffic
I think A .. Why should we correct on BOTH devices the ACL? Makes no sense
Provided answer seems to be correct.
'A', seems to be the correct answer here.
Traffic Selector mismatch, check the ACL for the interesting traffic on both nodes