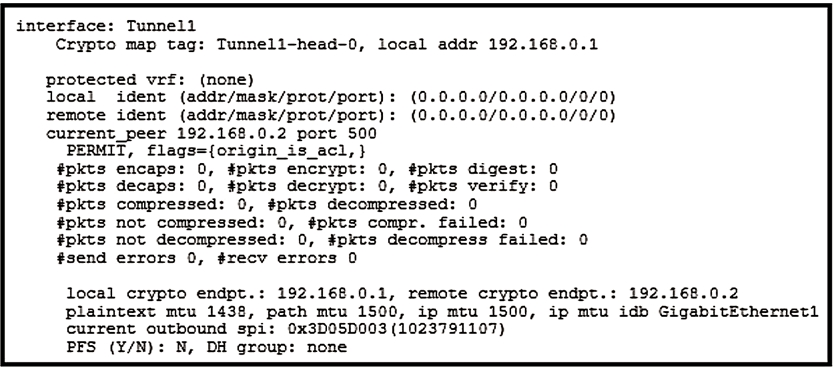
Refer to the exhibit. Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)

Refer to the exhibit. Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
The exhibit displays the output from the 'show crypto ipsec sa' command. The characteristics in the output point towards tunnel interfaces that use IPsec. Specifically, the 'local ident' and 'remote ident' fields showing 0.0.0.0/0.0.0.0/0/0 indicate a raw IPsec tunnel setup utilized by Virtual Tunnel Interface (VTI) and FlexVPN. Moreover, the exhibit does not indicate any references to protocol 47, which would be present if it were a GRE tunnel. Therefore, the correct tunnel types producing this output are FlexVPN and VTI.
i tested every answer in my lab and this is my finding. - only when a tunnel interface is used crypto map tag is Tunnel1-head-0 - only when tunnel mode is ipsec the local and remote ident are 0.0.0.0/0.0.0.0/0/0 - as soon as gre is used local and remote ident are (15.1.1.1/255.255.255.255/47/0) so i would choose D (FlexVPN with sVTI) and E (VTI when configured static)
FlexVPN is a Tunnel?
execuse me ? FlexVPN has Tunnel configuration as well. is you use GRE the NHRP will work and allow spoke-spoke , if you turn it as IPsec mode you will lose spoke-spoke and only hub-spoke will allow
B and E are correct. Remember crypto maps are applied to physical interfaces.
It asks for tunnel type. it should be C and E.
for whoever tested it in the lab, For flexvpn the output of show crypto ipsec sa, starts with the following: CSR1#show crypto ipsec sa interface: Virtual-Access // not interface: Tunnel0 So it should be B and E
You are correct about the name of the interface but I have not been able to recreate an ipsec SA with DMVPN where the x.x.x.x/x.x.x.x/47/0 port 47 is not showing
I got those results from LAB, only for DMVPN and VTI. VlexVPN has Virtual-access interface, NOT Tunnel interface. GRE-only tunnel doesnt use IPSEC so it wont show up in IPSEC SA command and Crypto map is not used for tunnel interfaces.
FlexVPN-Client#sh crypto ipsec sa interface: Tunnel0 Crypto map tag: Tunnel0-head-0, local addr 200.1.10.2 protected vrf: (none) local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) current_peer 200.1.10.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 200.1.10.2, remote crypto endpt.: 200.1.10.1 plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1/0 current outbound spi: 0xA9A19C6B(2845940843) PFS (Y/N): N, DH group: none
VTI#sh crypto ipsec sa interface: Tunnel0 Crypto map tag: Tunnel0-head-0, local addr 10.10.10.2 protected vrf: (none) local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) current_peer 12.12.12.2 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 10.10.10.2, remote crypto endpt.: 12.12.12.2 plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0 current outbound spi: 0x0(0) PFS (Y/N): N, DH group: none
Should be A and E, there is no reference to protocol 47 (GRE) in the output. Also the output shows acl, which implies crypto map. All of the local and remote idents are "0", indicating raw IPsec.
Analysing the result of the command 'show crypto ipsec sa', I received the same result for both Flexvpn and DMVPN. Therefore the correct answer is BD
D and E are correct. This output is from a Cisco FlexVPN client/server configuration. This is the client side with VTI !!!!
DMVPN#sh crypto ipsec sa interface: Tunnel0 Crypto map tag: Tunnel0-head-0, local addr 209.165.201.2 protected vrf: (none) local ident (addr/mask/prot/port): (209.165.201.2/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (192.0.2.3/255.255.255.255/47/0) current_peer 192.0.2.3 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3 #pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 209.165.201.2, remote crypto endpt.: 192.0.2.3 plaintext mtu 1458, path mtu 1500, ip mtu 1500, ip mtu idb (none) current outbound spi: 0xD1325E27(3509739047) PFS (Y/N): N, DH group: none
GETVPN#sh crypto ipsec sa interface: Ethernet0/0 Crypto map tag: GVPN-MAP, local addr 172.16.10.2 protected vrf: (none) local ident (addr/mask/prot/port): (10.0.0.0/255.252.0.0/0/0) remote ident (addr/mask/prot/port): (10.0.0.0/255.252.0.0/0/0) Group: GROUP5 current_peer 0.0.0.0 port 848 PERMIT, flags={} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.16.10.2, remote crypto endpt.: 0.0.0.0 plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0 current outbound spi: 0x3665FF29(912654121) PFS (Y/N): N, DH group: none
GRE-CRYPTO-MAP#sh crypto ipsec sa interface: Ethernet0/0 Crypto map tag: OUTSIDE-MAP, local addr 10.10.10.2 protected vrf: (none) local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0) current_peer 12.12.12.2 port 500 PERMIT, flags={origin_is_acl,ipsec_sa_request_sent} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 10.10.10.2, remote crypto endpt.: 12.12.12.2 plaintext mtu 1500, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0 current outbound spi: 0x0(0) PFS (Y/N): N, DH group: none
According to lab outputs A and E are correct
I built this in a lab and concur with nospampls results. Note that "show crypto ipsec sa" on a DMVPN will show port 47 as it is using mGRE. VTI with IKEv2 produces the 0.0.0.0/0.0.0.0/0/0 output as shown in the example. Since the question is asking for "tunnel" type that means only possible answers are D and E
crypto map is NOT a "tunnel type",. DMVPN and GETVPN are VPN types, Not Tunnel Types