Refer to the exhibit.
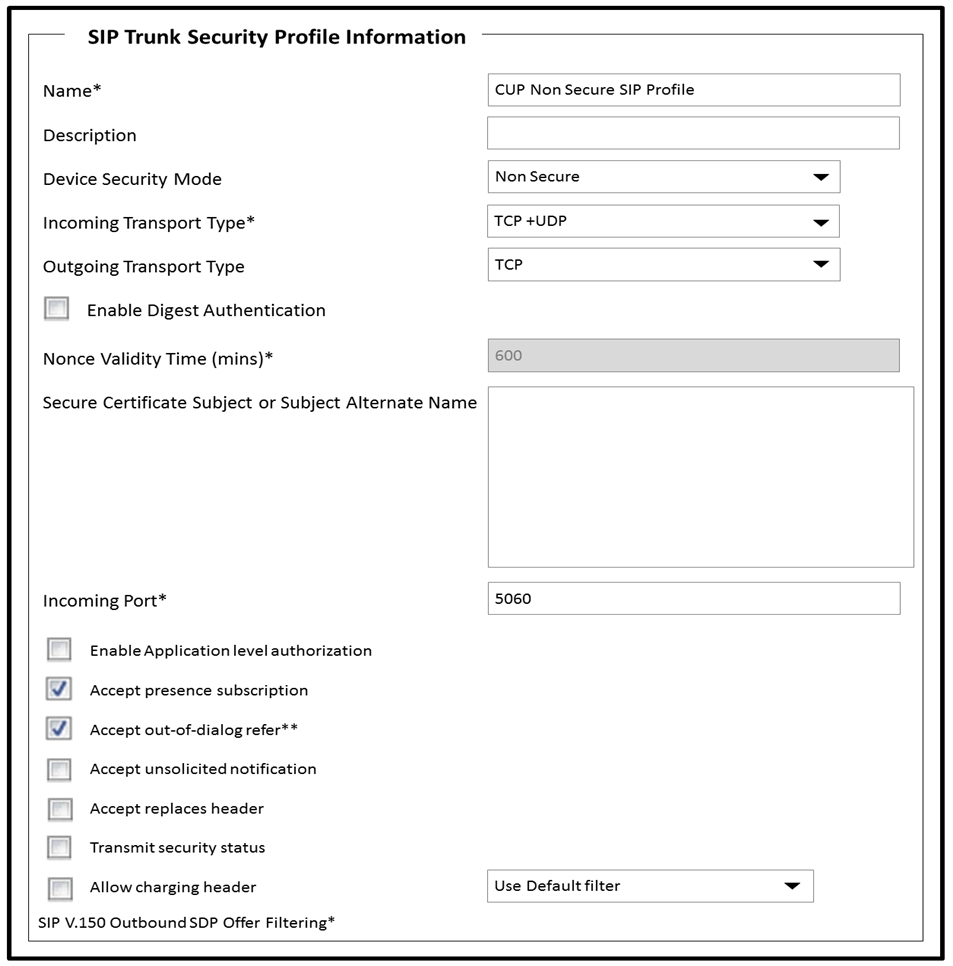
A collaboration engineer is configuring the Cisco UCM IM and Presence Service. Which two steps complete the configuration of the SIP trunk security profile?
(Choose two.)
Refer to the exhibit.

A collaboration engineer is configuring the Cisco UCM IM and Presence Service. Which two steps complete the configuration of the SIP trunk security profile?
(Choose two.)
To complete the configuration of the SIP trunk security profile for the Cisco UCM IM and Presence Service, you need to ensure certain settings are enabled for proper functionality. Checking the box to accept replaces header (Option A) and checking the box to accept unsolicited notification (Option E) are key configurations. Accepting the replaces header is essential for call transfer scenarios, and accepting unsolicited notifications helps in processing SIP NOTIFY messages, which are critical for presence and other instant messaging services.
Check the following check boxes: Accept Presence Subscription Accept Out-of-Dialog REFER Accept Unsolicited Notification Accept Replaces Header https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cucm/im_presence/configAdminGuide/11_5_1/cup0_b_config-and-admin-guide-1151su5/cup0_b_imp-system-configuration-1151su5_chapter_0111.html#task_441822D5A33E7A9AEB98901FCE5DA3D8
if i did not check anything what will happend