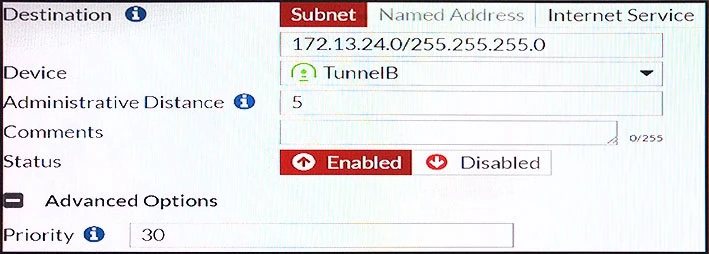
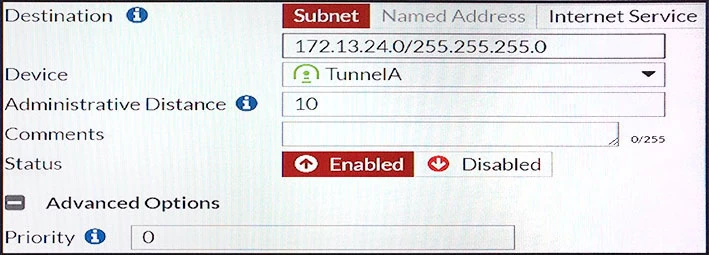
Which of the following statements are correct? (Choose two.)


Community votes
No votes yet
Community votes
No votes yet
Log messages are transmitted as plain text in LZ4 compressed format, and FortiGate can encrypt communications using SSL encrypted OFTP traffic to ensure secure transmission of log data to FortiAnalyzer. This makes options C and D correct as they align with the typical methods and security protocols used in transmitting log data from FortiGate to FortiAnalyzer.
Community votes
No votes yet
Community votes
No votes yet
The interface cannot be configured with an IP address if it is set up for one-arm sniffer because this mode is used for network traffic analysis and does not require an IP address. If the interface is a member of a virtual wire pair, it acts as a transparent bridge and does not need an IP address. When the operation mode is transparent, the device operates at Layer 2, meaning it forwards packets without needing an IP address assigned to its interfaces.
Community votes
No votes yet