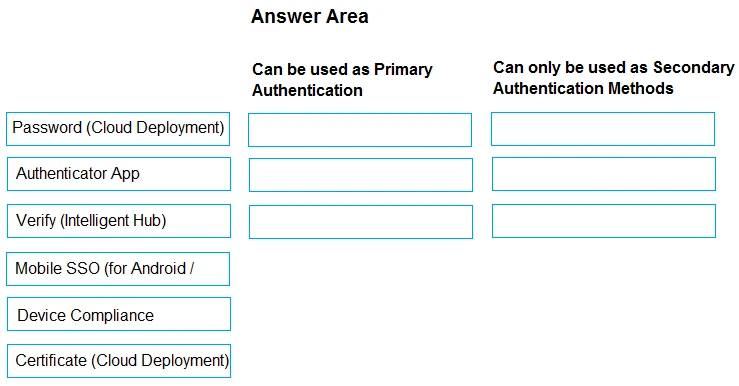
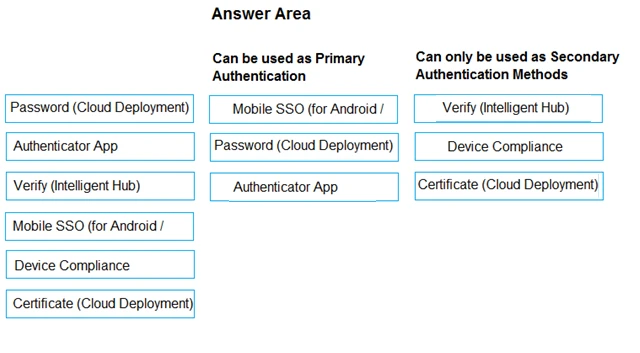
In Workspace ONE Access, some authentication methods can best be used as Primary Authentication, while others can only be used as Secondary Authentication.
Drag and drop the authentication methods on the left into the correct classification on the right.