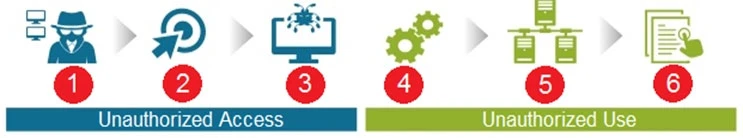
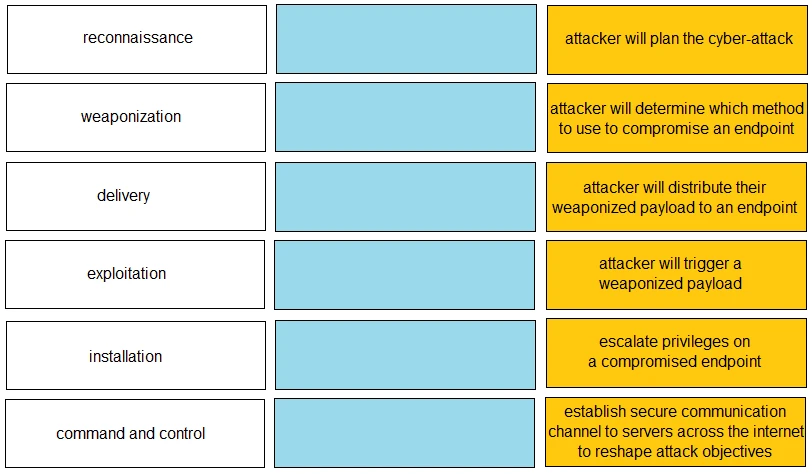
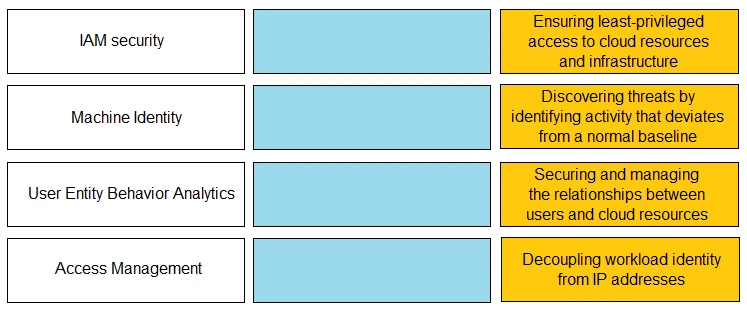
The suggested answer is D.
To secure applications against exploits on an endpoint, the most effective method is to apply software patches. These fixes address vulnerabilities in applications, operating systems, and firmware, reducing the risk of exploitation by malicious actors. This approach ensures that known security holes are sealed, keeping the systems protected against various types of attacks.