The Oracle Cloud Infrastructure (OCI) Audit service primarily captures and records changes related to OCI resources, including actions performed in the Oracle Cloud Infrastructure Console and REST API calls. It does not log changes within specific objects stored in an Object Storage bucket. Therefore, the statement that 'Changes within the objects stored in an Object Storage bucket are collected as Audit logs' is not valid.
They want resources in the other cloud provider to leverage OCI Autonomous Data Warehouse ML capabilities.
The connection between OCI and the other cloud provider should be provisioned as quickly as possible.
The connection should offer high bandwidth and predictable performance.
Which other cloud provider should you recommend to interconnect with OCI and meet the above requirements?
To meet the requirements of interconnecting Oracle Cloud Infrastructure (OCI) with another cloud provider in London, leveraging OCI Autonomous Data Warehouse ML capabilities, provisioning the connection quickly, and offering high bandwidth and predictable performance, the best recommendation is Microsoft Azure. This is due to the established partnership between Oracle and Microsoft, which includes the Oracle Interconnect for Microsoft Azure, allowing secure, low-latency, and high-bandwidth connections between the two providers.
What would happen if you choose not to proactively reboot the instance before the scheduled maintenance due date?
If you do not proactively reboot the instance before the scheduled maintenance due date, Oracle Cloud Infrastructure (OCI) will handle the maintenance for you. This can involve either reboot-migrating the instance to a different physical host or rebuilding the instance in place. The objective is to ensure that the necessary updates and maintenance are applied while minimizing downtime and impact to your instance.
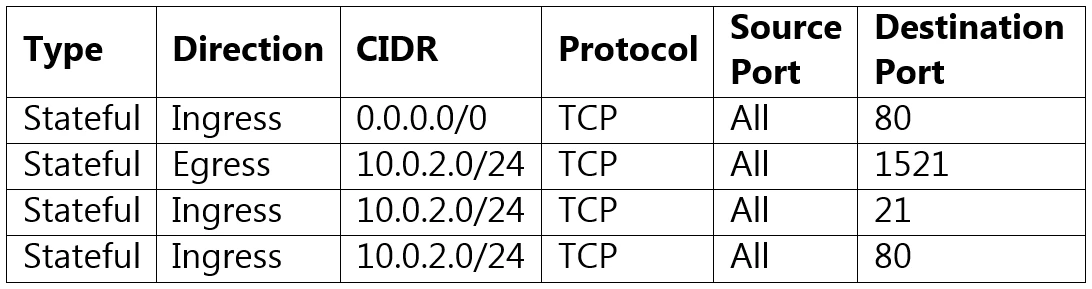
You have also created a network security group (NSG) as shown in the table here, and assigned it to your bastion host:
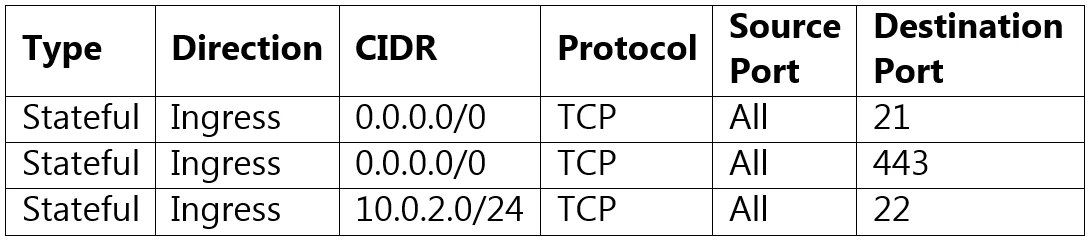
You have confirmed that routing is correct but when you SSH to the VM from your home over the Internet, you are unable to connect.
What could be the problem?
The problem is that SSH traffic (port 22) is not allowed in the security list nor on the network security group (NSG) from the Internet. For a user to SSH into the VM, there needs to be an ingress rule that allows traffic over port 22 from 0.0.0.0/0 (the Internet). The provided security list and NSG table only contain rules for ports 21, 80, 443, and 1521, none of which are for SSH. Therefore, SSH traffic is being blocked, leading to the inability to connect.
Each admin group has full access over their respective compartments as shown in the graphic below.
Your organization has set up a tag namespace, EmployeeGroup.Role and all your admin groups are tagged with a value of 'Admin'.
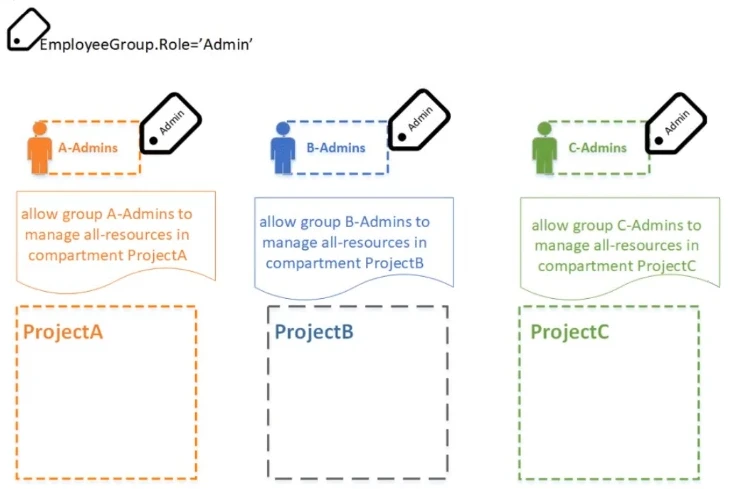
You want to set up a Test compartment for members of the three projects to share. You also need to provide admin access to all three of your existing admin groups.
Which policy would you write to accomplish this task?
In order to allow all three existing admin groups (A-Admins, B-Admins, C-Admins) to have admin access to the Test compartment based on their 'Admin' tags, the proper policy needs to specify the dynamic group condition. The correct policy syntax is: 'Allow dynamic-group to manage all-resources in compartment Test where request.principal.group.tag.EmployeeGroup.Role='Admin''. This condition ensures that any member of a group tagged with 'Admin' can manage resources in the Test compartment. Other options are incorrect as they either use non-existent keywords or do not correctly specify the conditions needed to grant the access.