Question 6 of 90
An administrator wants to secure the connection between an HP Provision switch and HP VAN SDN Controller. What is the recommended approach to securing the OpenFlow messages?
Suggested Answer: A
Community votes
No votes yet
Question 7 of 90
A customer has a network consisting of 90 switches running OpenFlow 1.0. High Availability is not required as a hybrid network is being used. Which license types does the customer need to purchase? (Select two.)
Suggested Answer: D, E
Community votes
No votes yet
Question 8 of 90
An SDN developer wants to develop a new OpenFlow proactive application using the HP VAN SDN Controller. The controller is configured with IP address
192.168.56.7 and is using release 2.0. The developer is unsure of the REST APIs available on the controller.
To which URL should you recommend the developer navigate?
192.168.56.7 and is using release 2.0. The developer is unsure of the REST APIs available on the controller.
To which URL should you recommend the developer navigate?
Suggested Answer: A
Community votes
No votes yet
Question 9 of 90
A customer wants to deploy an HP ProVision-based network with laptops daisy chained to physical IP phones. The customer also wants the laptop traffic to be managed by OpenFlow, while the phones use traditional QoS. Which OpenFlow switch instance configuration option should the customer use?
Suggested Answer: C
Community votes
No votes yet
Question 10 of 90
What is an advantage of using the HP Network Optimizer SDN application with UC&C applications rather than just the SDN applications?
Suggested Answer: D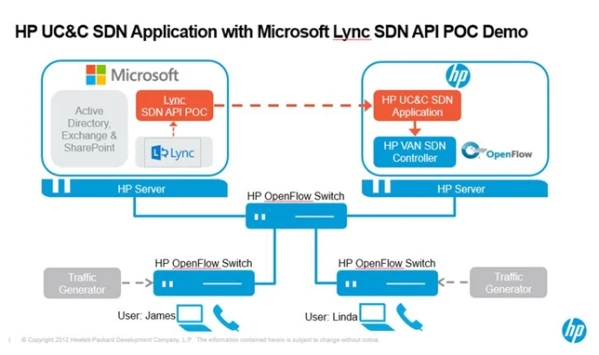
The first capability that's implemented is the ability of the Lync server (or any communications server, potentially) to dynamically provide to the network controller the IP addresses/ports of the paired endpoints of a real time flow. This enables the network to mark, without deep packet inspection, those flows with a CoS/QoS tag that will give them the proper treatment in the network. This becomes a positive identification of "authorized" real-time flows; any device/flow trying to use that tagging that is not "authorized" through the API can automatically be re-tagged to a best effort service class.
This technique has a number of critical advantages over current techniques. When compared to the typical VLAN, it enables positive tagging of a variety of devices, including BYOD and potentially other systems that might have multiple traffic types (e.g., a PC running a soft client or a tablet).
In addition, when compared to deep packet inspection at each access element, it reduces cost as well as eliminating the errors and complexity that encryption of the packet stream can introduce.
Reference: HP and Microsoft Demo OpenFlow-Lync Applications-optimized Network D

The first capability that's implemented is the ability of the Lync server (or any communications server, potentially) to dynamically provide to the network controller the IP addresses/ports of the paired endpoints of a real time flow. This enables the network to mark, without deep packet inspection, those flows with a CoS/QoS tag that will give them the proper treatment in the network. This becomes a positive identification of "authorized" real-time flows; any device/flow trying to use that tagging that is not "authorized" through the API can automatically be re-tagged to a best effort service class.
This technique has a number of critical advantages over current techniques. When compared to the typical VLAN, it enables positive tagging of a variety of devices, including BYOD and potentially other systems that might have multiple traffic types (e.g., a PC running a soft client or a tablet).
In addition, when compared to deep packet inspection at each access element, it reduces cost as well as eliminating the errors and complexity that encryption of the packet stream can introduce.
Reference: HP and Microsoft Demo OpenFlow-Lync Applications-optimized Network D
Community votes
No votes yet