In this scenario, which two methods will satisfy the requirement? (Choose two.)
To access the JSON API on FortiManager and retrieve information on an object, you can use methods that interact with APIs directly. Using the curl utility from your workstation allows you to make HTTP requests to the API and receive the data in JSON format, making it a suitable method. Similarly, making a call with a web browser on your workstation can also send HTTP requests to the API endpoint and retrieve data in JSON format. Downloading a WSDL file and using SoapUI is more aligned with SOAP-based APIs rather than JSON APIs.
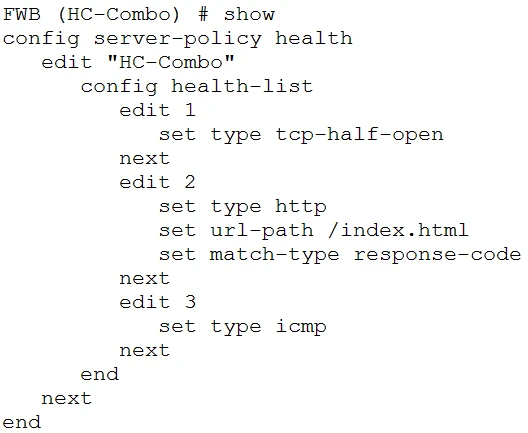
You created a custom health-check for your FortiWeb deployment.
Given the output shown in the exhibit, which statement is true?
The custom health-check configuration includes three types of checks: TCP half-open, HTTP, and ICMP. The HTTP check specifically mentions matching the response code of the URL path '/index.html'. Therefore, the FortiWeb must receive an HTTP 200 response code from the server to pass this check.
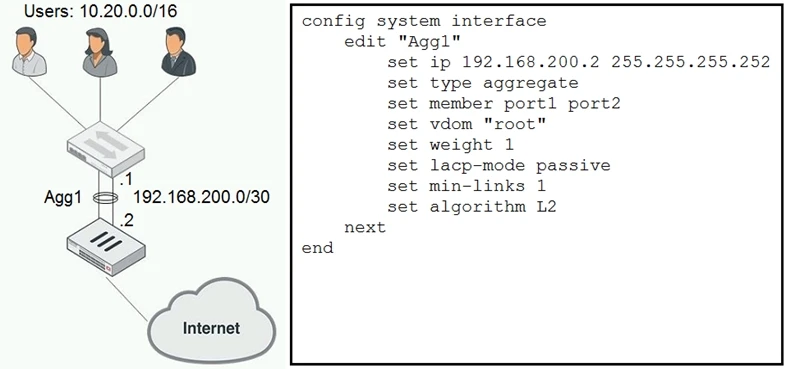
You created an aggregate interface between a FortiGate and a switch consisting of two 1 Gbps links as shown in the exhibit. However, the maximum bandwidth never exceeds 1 Gbps and employees are reporting that the network is slow. After troubleshooting, you notice that only one member interface is being used. The configuration for the aggregate interface is shown in the exhibit.
In this scenario, which command will solve this problem?
A.
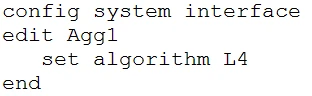
B.
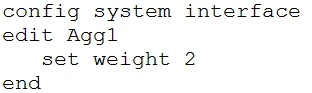
C.
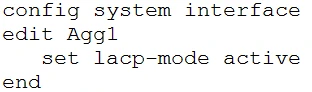
D.
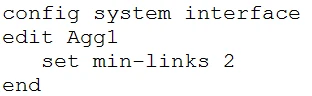
The problem mentioned indicates that only one member interface is being used in the aggregate link, which implies that the load is not being properly balanced across both links. The current configuration uses the 'L2' algorithm for balancing, which might not be ensuring an appropriate distribution of traffic across both links. To resolve this issue, changing the load balancing algorithm to 'L4' can be more effective. The L4 algorithm allows for better load distribution by considering both layer 2 (MAC/IP) and layer 3 (TCP/UDP port) headers. Therefore, the correct command to solve this problem is: config system interface edit Agg1 set algorithm L4 end.
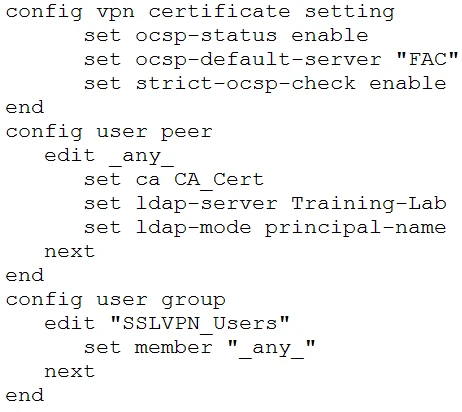
A FortiGate device is configured to authenticate SSL VPN users using digital certificates. A partial FortiGate configuration is shown in the exhibit.
Referring to the exhibit, which two statements about this configuration are true? (Choose two.)
The configuration is set to use the Online Certificate Status Protocol (OCSP) to verify the status of user certificates and requires the certificates to contain specific information. The authentication will fail if the user certificate does not contain the User Principal Name (UPN) information because this is specified in the configuration under the ldap-mode principal-name setting. Additionally, authentication will fail if the OCSP server is down, as the OCSP status is enabled and strict checking is required. OCSP does not verify if a certificate has expired but validates if the certificate has been revoked.
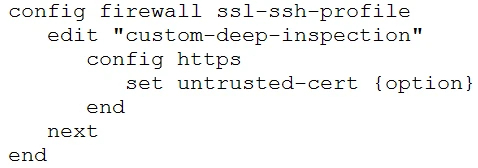
Which command-line option for deep inspection SSL would have the FortiGate re-sign all untrusted self-signed certificates with the trusted Fortinet_CA_SSL certificate?
To have the FortiGate re-sign all untrusted self-signed certificates with the trusted Fortinet_CA_SSL certificate during deep inspection SSL, the 'ignore' option should be used. This option changes untrusted certificates to trusted ones.