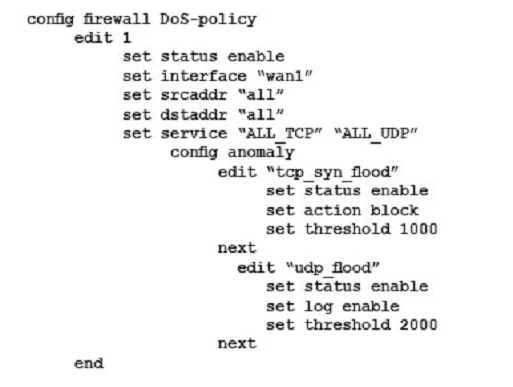
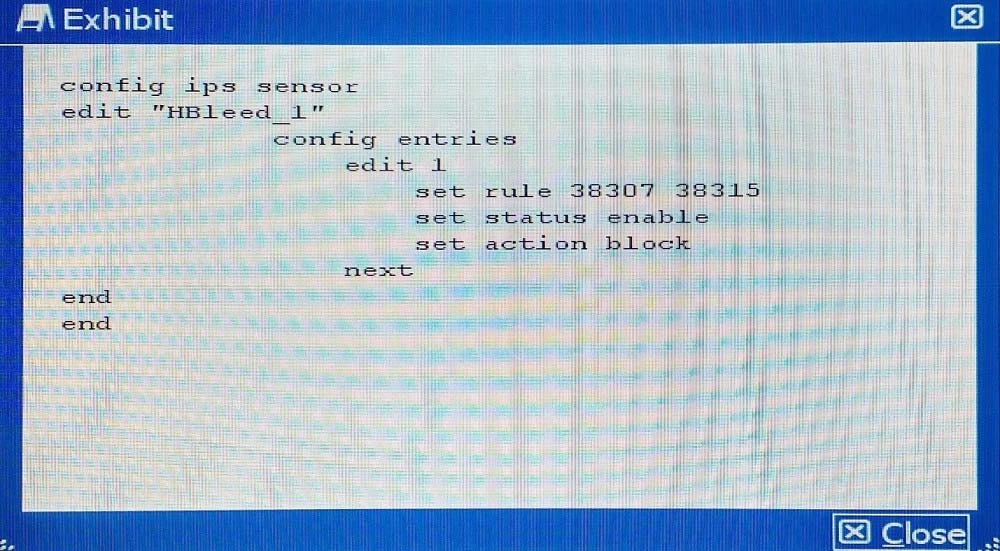
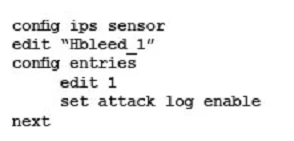
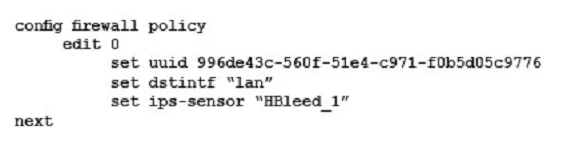
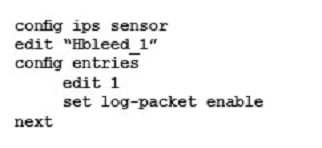
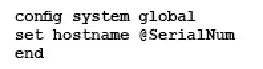
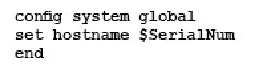
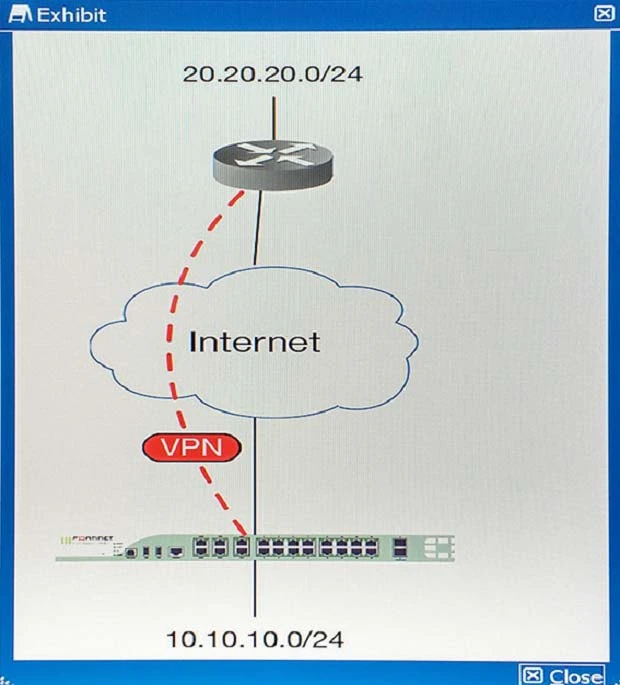
- The interface to the Internet is on WAN1.
- There is no requirement to specify which addresses are being protected or protected from.
- The protection is to extend to all services.
- The tcp_syn_flood attacks are to be recorded and blocked.
- The udp_flood attacks are to be recorded but not blocked.
- The tcp_syn_flood attacks threshold is to be changed from the default to 1000.
The exhibit shows the current DoS-policy.
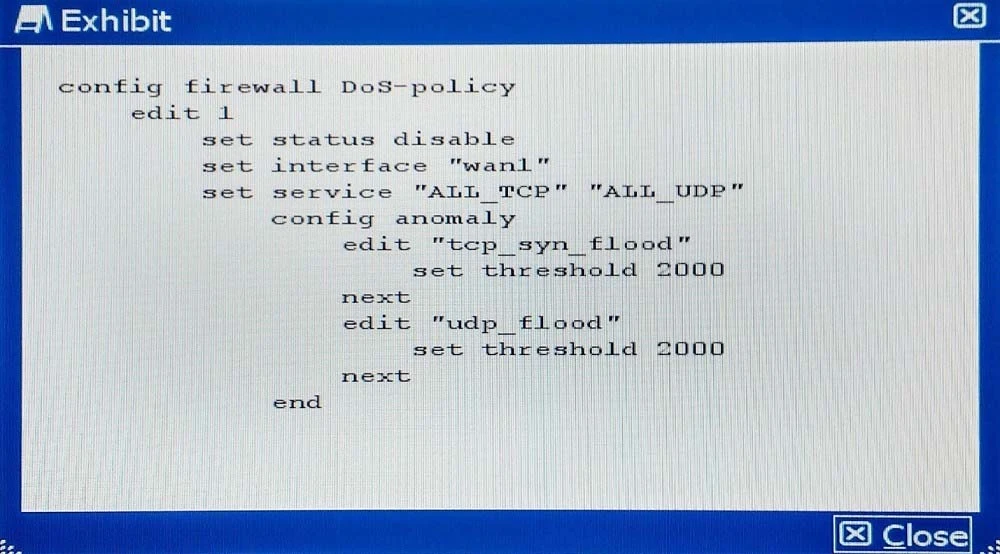
Which policy will implement the project requirements?
A)

B)

C)
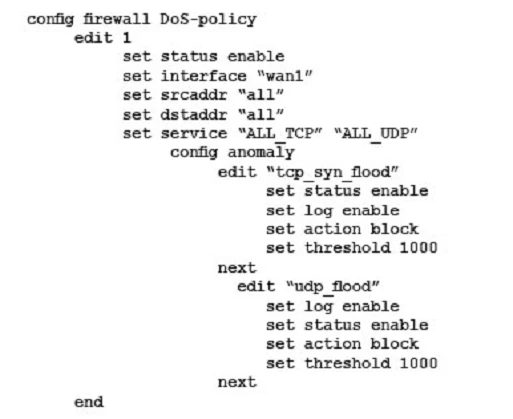
D)