In a wireless network integration, FortiNAC obtains connecting MAC address information using MAC notification traps. This method allows the system to receive updates whenever a new device connects to the network, ensuring accurate and up-to-date information about connected devices.
In a typical Operational Technology (OT) environment, common breach points include black hat activities which involve malicious attackers, hard hat incidents that involve physical security breaches by insiders or on-site personnel, and RTU (Remote Terminal Unit) exploits which are vulnerabilities in critical field devices used for automating industrial processes.
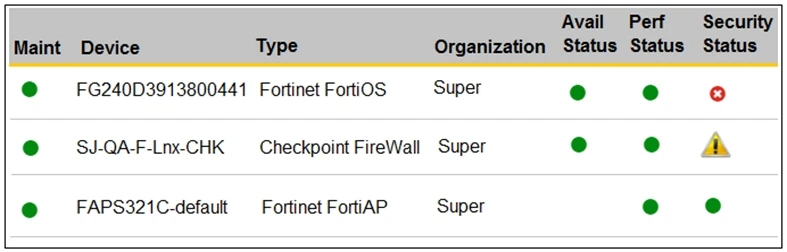
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
The exhibit presents a status overview of various network devices. The security status icon of the FortiGate device shows a red cross, indicating one or more high-severity security incidents. This information is typically viewed in the summary dashboard, which provides a consolidated view of device statuses, including security alerts.
Which two methods should the administrator use to achieve this? (Choose two.)
To implement active authentication, an OT network administrator should use two-factor authentication on FortiAuthenticator and local authentication on FortiGate. Two-factor authentication is a robust method that involves verifying user identity through two separate channels or forms of credentials, making it an active form of authentication. Local authentication on FortiGate also qualifies as active authentication because it requires users to actively enter credentials verified against locally stored databases.
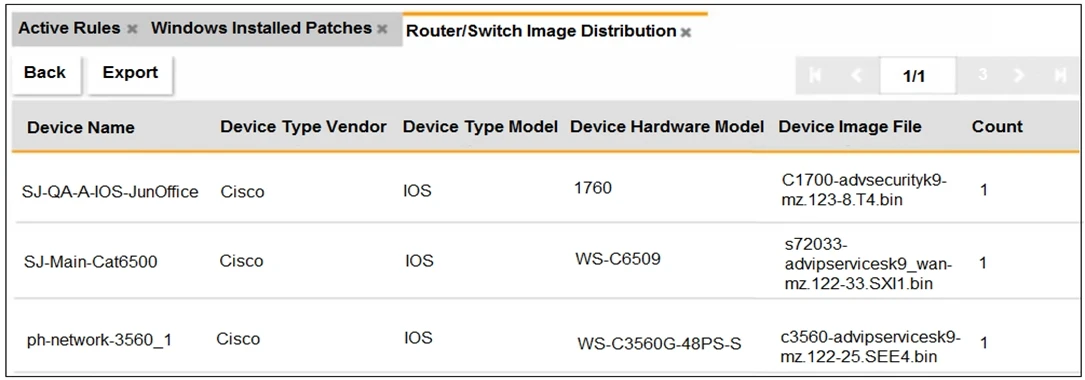
An OT administrator ran a report to identify device inventory in an OT network.
Based on the report results, which report was run?
Based on the report details, it displays the device name, vendor, model, hardware model, and the device image file, all relevant to an inventory of devices. This comprehensive information aligns well with what a FortiSIEM CMDB (Configuration Management Database) report would provide. Such a report is specifically designed to capture detailed information about devices in the network, making option A the correct answer.