The issue described involves the FortiGate deleting sessions after clients send SYN packets but before receiving the SYN/ACK packets. This indicates a problem with how long half-open TCP sessions (sessions where the handshake is not yet complete) are kept alive. To fix this, increasing the TCP half open session timer would allow more time for the SYN/ACK packets to arrive and complete the handshake before the session is terminated.
What information is included in the output of the sniffer? (Choose two.)
When running the command 'diagnose sniffer packet any "host 10.0.2.10" 2' on a FortiGate, the sniffer captures packets with a verbosity level of 2. At this level, the output includes the IP headers and the IP payload of the packets. Specifically, verbosity level 2 includes header information up to the IP layer and the actual data being transmitted in the IP payload. Ethernet headers are included in verbosity level 3 and above, while port names are not included in this output.

Based on the above outputs, which is the FortiGuard web filter category for the web site www.fgt99.com?
The FortiGuard web filter category for the website www.fgt99.com is 52, corresponding to Information Technology. The hex value 34000000 converts to decimal 52.
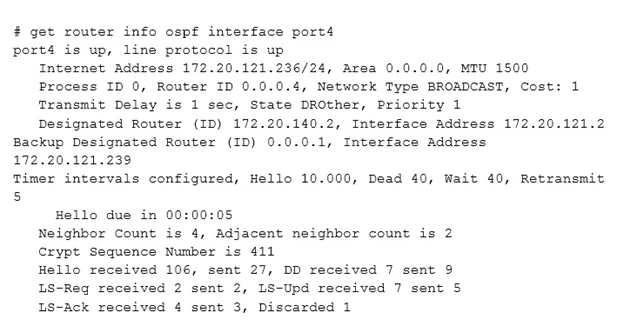
Which statements are true regarding the above output? (Choose two.)
The port4 interface is in OSPF backbone area, this is verified by the area ID 0.0.0.0 mentioned. Additionally, the neighbor count being 4 along with an adjacency count of 2 indicates that there are at least five OSPF routers in the port4 network: the local router and its four neighbors.
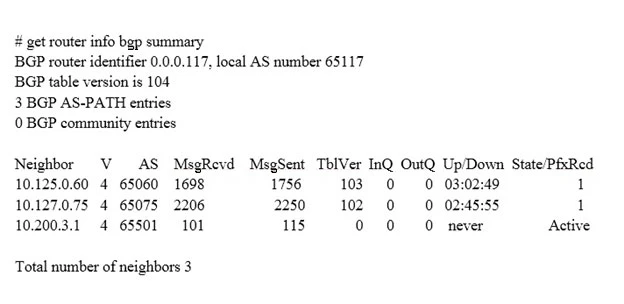
Which statements are true regarding the output in the exhibit? (Choose two.)
The BGP state of the peer 10.125.0.60 is Established, as indicated by the Up/Down time of 03:02:49 and a prefix received count of 1. This confirms that the BGP session is successfully established with this peer. On the other hand, the BGP peer 10.200.3.1 is in the 'Active' state, which means it has not established a TCP connection. This also implies that the local BGP peer has not received an OpenConfirm from 10.200.3.1.