What could have caused this problem?
The FortiClient MST file is essential as it passes the customized configuration settings to the MSI installer package. If the FortiClient MST file is missing from the distribution package, the custom configuration would not be applied, leading to the issue of missing custom configurations after deployment.
What is the default behavior of real-time protection control?
When FortiClient is installed on a Windows Server, the default behavior is to have real-time protection disabled. This is a standard security measure to prevent potential conflicts with server-related applications and to ensure the server's performance and stability.

What can you conclude from the log message?
The log details indicate that the remote user connection is blocked due to a policy violation, with the specific message stating 'Denied: failed to match an API-gateway.' This failure to match an API-gateway is an indication that no ZTNA firewall policy aligns with the connection attempt. ZTNA firewall policies are responsible for access control by matching and redirecting client requests. Therefore, the conclusion is that the remote user connection does not match the ZTNA firewall policy.
FortiClient anti-exploit detection terminates the compromised application process when it detects exploits. This action is taken to immediately stop any malicious activity and prevent the exploit from executing further.
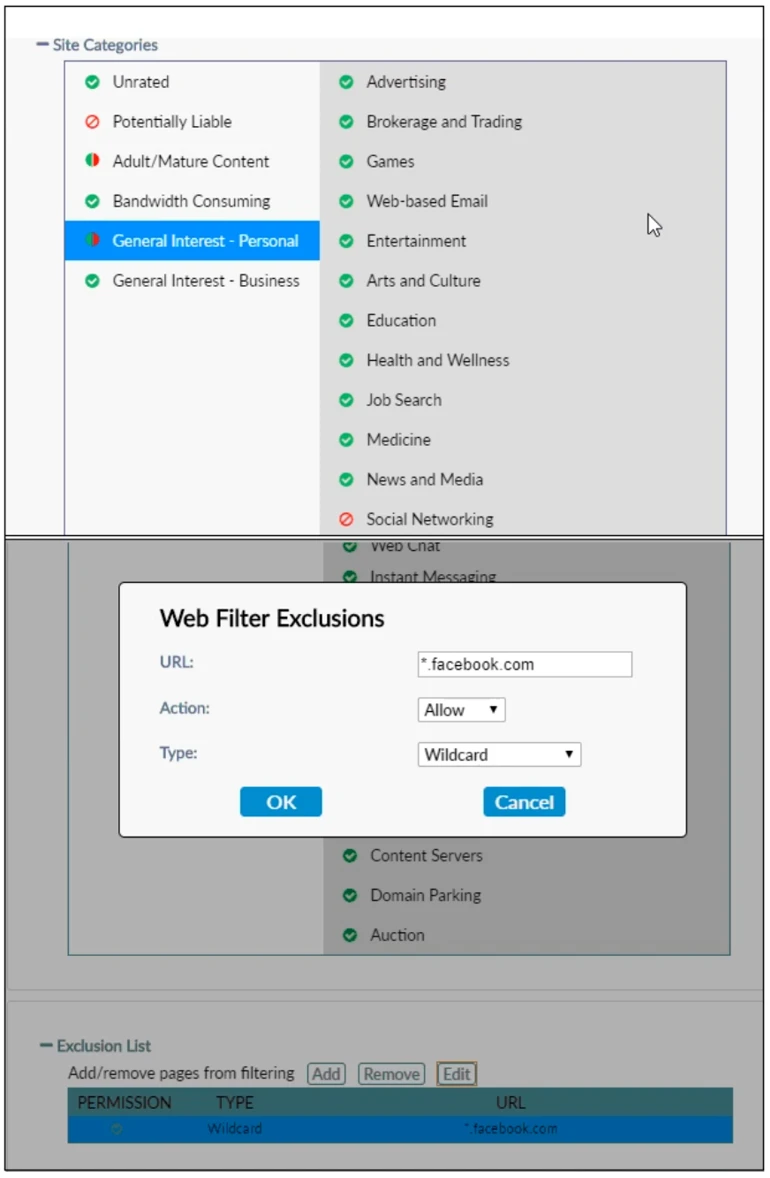
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook.com?
Based on the settings shown in the exhibit, FortiClient will allow access to Facebook. The exclusion list specifically includes a wildcard entry for *.facebook.com with the action set to 'Allow,' which means any attempt to access Facebook or its subdomains will be permitted.