The security policy that has all of its rules disabled by default is Device Control. This policy typically includes rules regarding the use and management of external devices like USB drives, and these rules are not enabled by default to allow users flexibility in configuring the controls as needed.
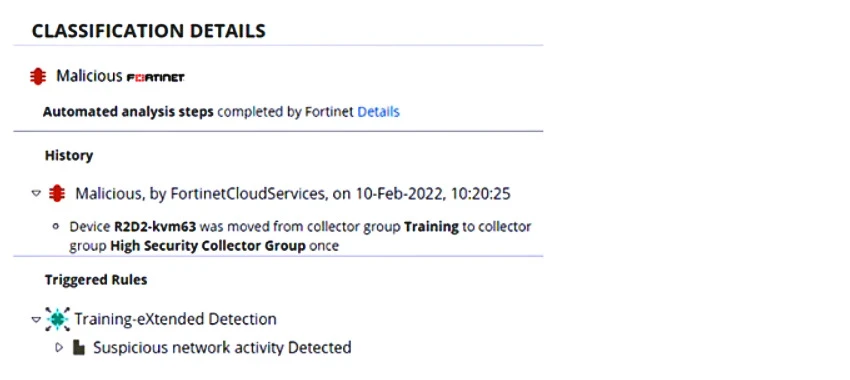
The event is related to Training-eXtended Detection, which operates in simulation mode, and the playbooks are configured for this event, indicated by the device being moved automatically between collector groups.
The correct connectors for FortiEDR automated incident response are FortiNAC and FortiGate. FortiNAC offers network access control, essential for isolating and controlling endpoints during incident response. FortiGate, a next-generation firewall, provides advanced security measures, traffic control, and threat management, which are crucial for handling security incidents automatically. These integrations enhance FortiEDR’s capabilities for effective incident management.
The FortiEDR Threat Hunting Repository is the component specifically designed to find and delete known malware on any device within the system. It is tailored for the purpose of identifying and eliminating malicious files across the entire network, hence making it the appropriate choice for this function.
The Comprehensive threat hunting profile is the most resource-intensive because it involves collecting almost all data from endpoints. This extensive data collection process requires more resources compared to other profiles, making it the most demanding in terms of resource utilization.