Question 6 of 38
In public key infrastructure (PKI), what is the primary role of a certificate revocation list (CRL)?
Correct Answer: D
Question 7 of 38
A conference center wireless network provides guest access through a captive portal, allowing unregistered users to self-register and connect to the network.
The IT team has been tasked with updating the existing configuration to enforce captive portal authentication over a secure HTTPS connection.
Which two steps should the administrator take to implement this change? (Choose two.)
The IT team has been tasked with updating the existing configuration to enforce captive portal authentication over a secure HTTPS connection.
Which two steps should the administrator take to implement this change? (Choose two.)
Correct Answer: A, B
Question 8 of 38
Which two broad categories must be considered for wireless troubleshooting when evaluating key wireless metrics?
Correct Answer: D
Question 9 of 38
Refer to the exhibits.
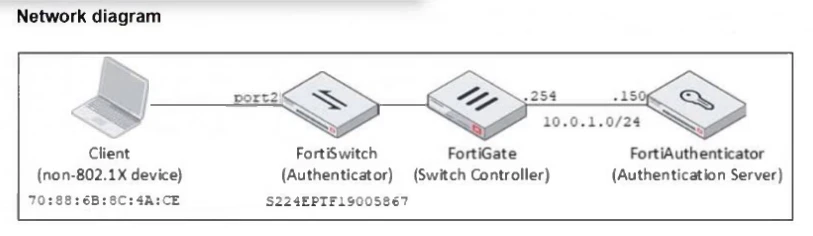
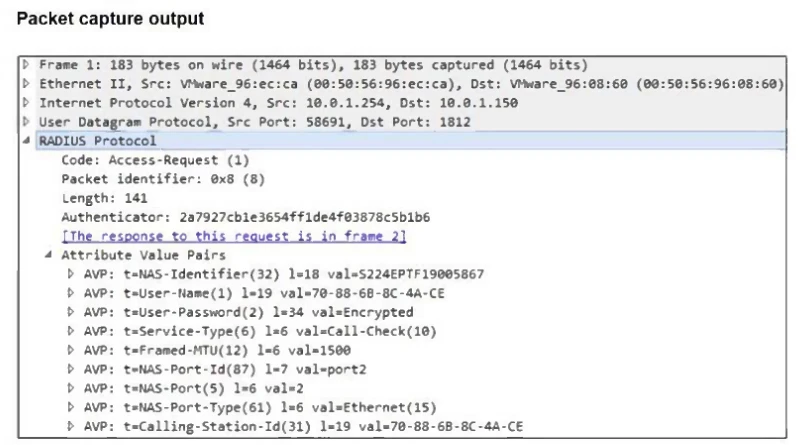
Examine the network diagram and packet capture shown in the exhibit.
During packet capture analysis, a RADIUS Access-Request packet was detected being sent from FortiSwitch to FortiAuthenticator and passing through FortiGate. The capture shows that the User-Name attribute in the RADIUS Access-Request packet contains the client MAC address.
Why is the client MAC address contained in the User-Name attribute of the RADIUS Access-Request packet?


Examine the network diagram and packet capture shown in the exhibit.
During packet capture analysis, a RADIUS Access-Request packet was detected being sent from FortiSwitch to FortiAuthenticator and passing through FortiGate. The capture shows that the User-Name attribute in the RADIUS Access-Request packet contains the client MAC address.
Why is the client MAC address contained in the User-Name attribute of the RADIUS Access-Request packet?
Correct Answer: C
Question 10 of 38
How does the Syslog-based single sign-on (SSO) feature in FortiAuthenticator function to correlate user activity with authentication events across multiple network devices?
Correct Answer: A