Question 6 of 57
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Correct Answer: A, B
Question 7 of 57
Refer to the exhibits.
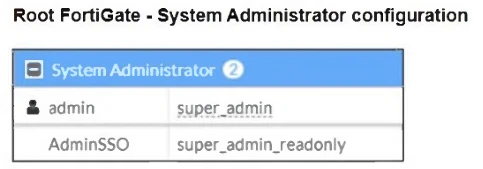
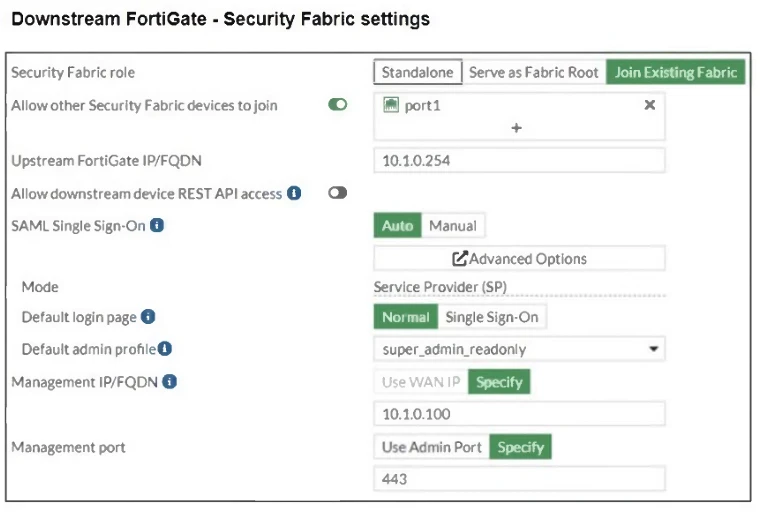
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?


The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
Correct Answer: C
Question 8 of 57
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Correct Answer: D
Question 9 of 57
Refer to the exhibit, which shows an ADVPN network.
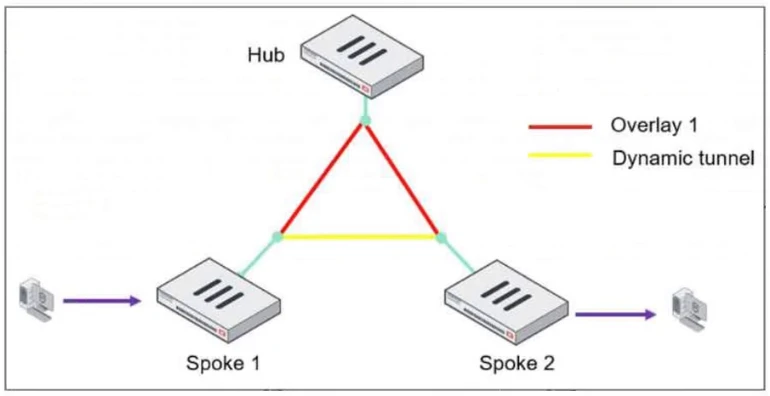
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?

The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
Correct Answer: B
Question 10 of 57
What is the initial step performed by FortiGate when handling the first packets of a session?
Correct Answer: C