Question 6 of 200
Which of the following appendices gives detailed lists of all the technical terms used in the report?
Correct Answer: D
Question 7 of 200
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet. The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
During external penetration testing, which of the following scanning techniques allow you to determine a ports state without making a full connection to the host?

During external penetration testing, which of the following scanning techniques allow you to determine a ports state without making a full connection to the host?
Correct Answer: B
Question 8 of 200
Passwords protect computer resources and files from unauthorized access by malicious users. Using passwords is the most capable and effective way to protect information and to increase the security level of a company.
Password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system to gain unauthorized access to a system.
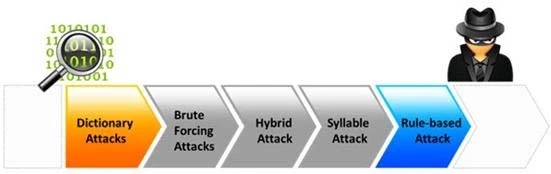
Which of the following password cracking attacks tries every combination of characters until the password is broken?
Password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system to gain unauthorized access to a system.

Which of the following password cracking attacks tries every combination of characters until the password is broken?
Correct Answer: A
Question 9 of 200
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.

What is the last step in preparing a Rules of Engagement (ROE) document?

What is the last step in preparing a Rules of Engagement (ROE) document?
Correct Answer: C
Question 10 of 200
Which of the following is a framework of open standards developed by the Internet Engineering Task Force (IETF) that provides secure transmission of the sensitive data over an unprotected medium, such as the Internet?
Correct Answer: D