A key advantage of cloning a virtual machine (VM) is that it reduces the time required to create multiple copies of a VM. Cloning allows administrators to quickly create replicas of a VM without going through the lengthy process of setting up the operating system and installing applications from scratch each time. This efficiency is particularly useful when deploying several VMs with the same configuration.
Which IDPS technique uses a database that contains known attack patterns?
Signature-based IDPS technique uses a database containing known attack patterns. This method matches incoming data with known signatures of past attacks. It is effective for identifying threats that have been previously documented.
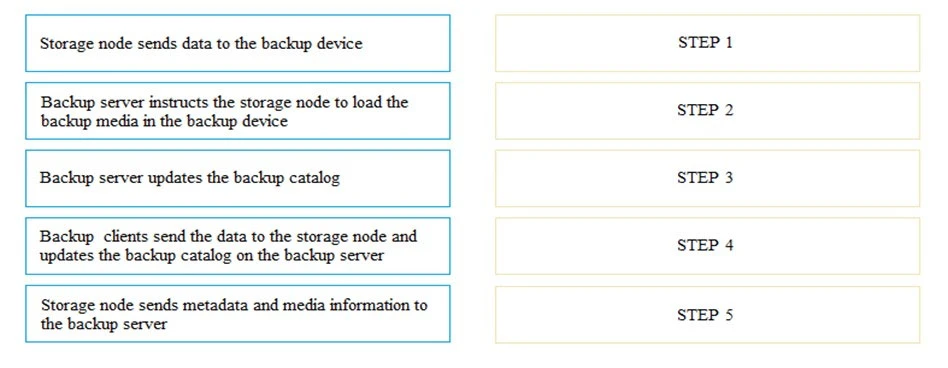
In a backup operation, what are the correct sequence of steps after the backup server initiates the scheduled backup process?
Select and Place:
In a content addressable storage (CAS) system, a content address (CA) is created from the binary representation of an object. This means that the CA is derived from the data content itself, ensuring a unique and consistent address for each piece of stored content. This method eliminates the need to manage the physical location of the data within the storage system.
Link aggregation optimizes fabric performance by distributing network traffic across ISLs. This helps in improving overall network efficiency and avoiding congestion by making better use of available bandwidth. It ensures that traffic is evenly distributed, preventing any single link from becoming a bottleneck.