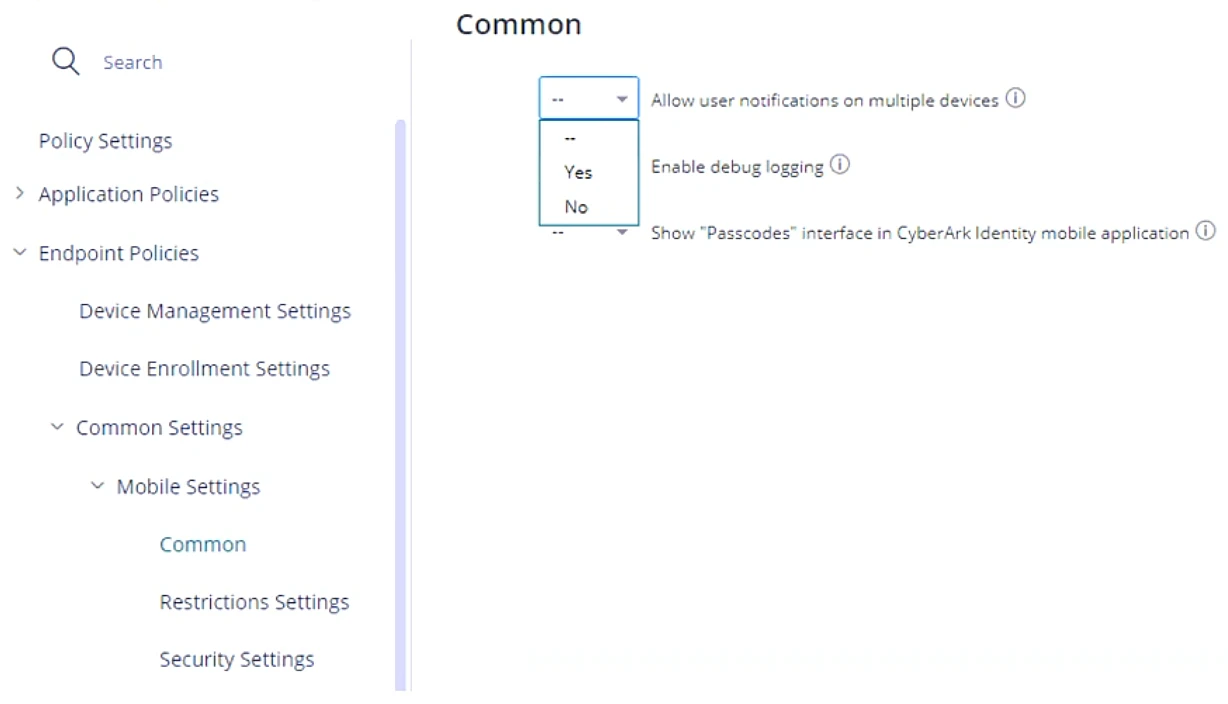
Which configuration can help achieve this?
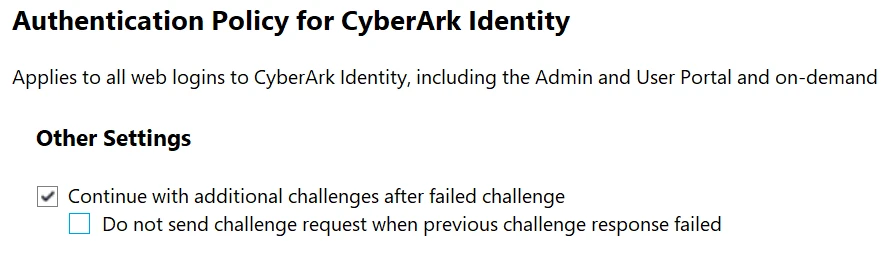
Which statements are correct regarding this Authentication Policy? (Choose two.)
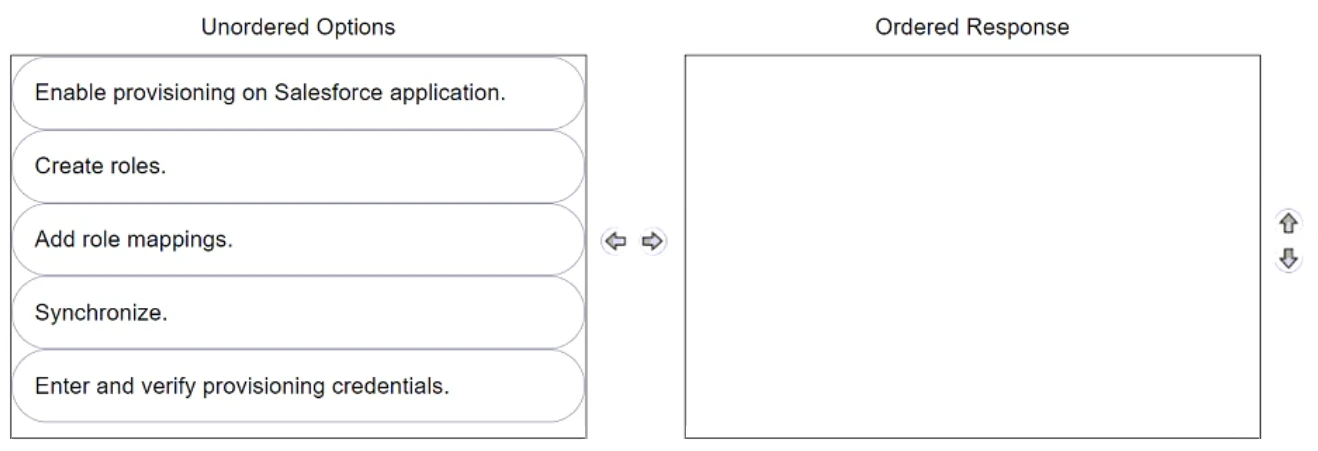
Your organization wants to automatically create user accounts with different Salesforce licenses (e.g., Salesforce, Identity, Chatter External).
In CyberArk Identity, arrange the steps to achieve this in the correct sequence.
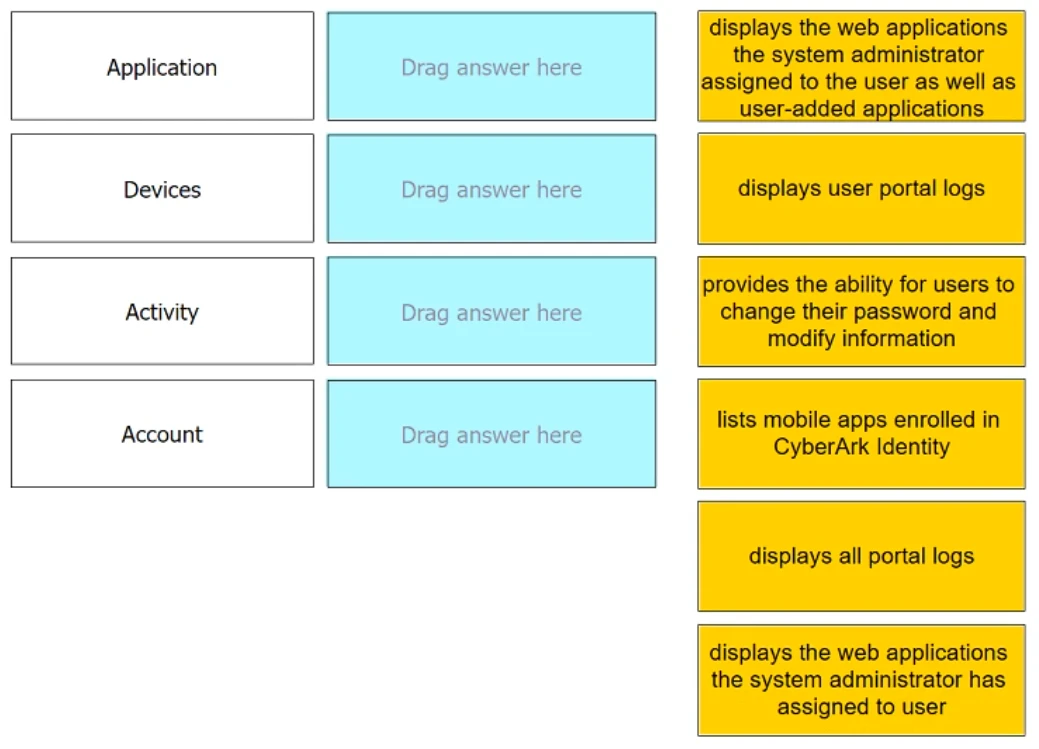
Match each User Portal tab to the correct description.
Within the "Allow user notifications on multiple devices", if you leave the setting as Default (--), what happens if a user triggers a MFA Push notification and has enrolled three different devices?