If a company has implemented encryption for hard drives on its servers as part of a data loss prevention strategy, one logical additional step would be to ensure all network traffic is encrypted as well. This ensures that data is protected not only at rest but also while in transit, reducing the risk of data interception and loss during communication between devices or over the internet. Encrypting network traffic complements the overall data protection strategy by covering another potential vulnerable point where data could be compromised.
Community votes
No votes yet
According to RFC 1918, certain IP address ranges are reserved for private use and cannot be routed on the public internet. These ranges are: 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255. The IP address 172.16.19.241 falls within the 172.16.0.0 to 172.31.255.255 range, making it a valid private IP address in compliance with RFC 1918.
Community votes
No votes yet
To perform bare-metal maintenance on a server in a remote datacenter, an administrator would need access to the server's console at a hardware level, bypassing the operating system. An IP KVM (Keyboard, Video, Mouse) is a device that provides remote access to the physical server's console, allowing the administrator to interact with the server as if they were physically present at the keyboard and monitor. IP KVMs are designed specifically for remote management of servers and allow access even when the operating system is not running.
Community votes
No votes yet
To provide a VM with high availability, the technician should clone the original VM. Cloning creates an identical copy of the VM, which can be used in a failover scenario to minimize downtime. Taking a snapshot only captures the state of the VM at a particular point in time and is primarily used for backup or recovery purposes, not for ensuring ongoing availability. Converting to dynamic disks or performing a P2V migration does not directly contribute to high availability. Cloning and incorporating the clone into a failover cluster is the most effective way to achieve high availability.
Community votes
No votes yet
Which of the following commands should the administrator use to resolve the issue without granting unnecessary permissions?
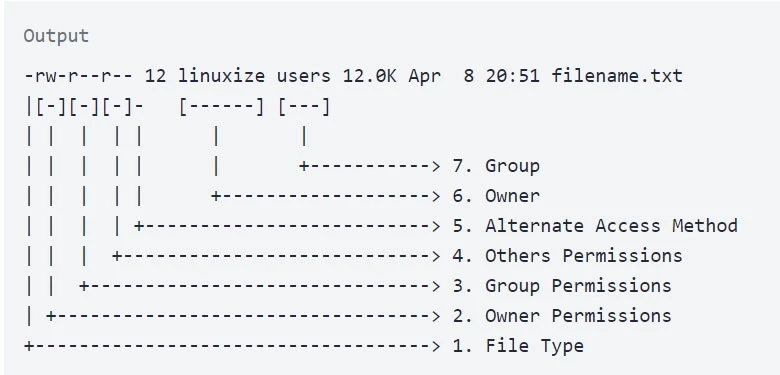
https://linuxize.com/post/what-does-chmod-777-mean/
 D
DCommunity votes
No votes yet