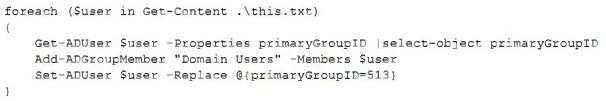
Which of the following scripting languages was used in the script?

The script provided uses cmdlet names that follow a Verb-Noun format, such as 'Get-ADUser', 'Add-ADGroupMember', and 'Set-ADUser', which are distinctive features of PowerShell. Additionally, the use of the pipeline operator '|' to pass objects between commands is a common characteristic of PowerShell. The script also interacts with Active Directory, which is commonly administered using PowerShell cmdlets in Windows environments. Therefore, the scripting language used in the script is PowerShell.
The observed activity where users sometimes access the company's internal portal via HTTP (port 80) and other times via HTTPS (port 443) suggests an on-path attack. This type of attack is typically performed by someone with internal access and involves intercepting and manipulating network traffic. By forcing users to use HTTP instead of HTTPS, the attacker can capture sensitive information transmitted over the network, which aligns with the user's accounts being compromised.
The security policies prioritize confidentiality over availability and external systems over internal ones. Both CAP.SHIELD and THANOS.GAUNTLET have the same CVSS scores with high confidentiality impact, but CAP.SHIELD is on an external system, making it the highest priority to patch according to the policies.
A Business Continuity Plan (BCP) is essential to ensure that mission-critical services are available in the event of an incident. While disaster recovery focuses on restoring IT infrastructure and operations post-disaster, a business continuity plan encompasses a broader range of strategies aimed at maintaining essential functions during and after any unplanned incident, ensuring minimal disruption to operations.
To eliminate and reduce shadow IT in the enterprise and manage high-risk cloud applications, the most effective solution is to deploy a Cloud Access Security Broker (CASB) and enable policy enforcement. A CASB provides visibility and control over the use of cloud services, helping to identify and manage shadow IT. It enforces security policies to ensure compliance and protect against threats, thereby reducing the risk associated with unauthorized cloud application usage.