Question 6 of 408
Company A is merging with Company B. Company A is a small, local company. Company B has a large, global presence. The two companies have a lot of duplication in their IT systems, processes, and procedures. On the new Chief Information Officer's (CIO's) first day, a fire breaks out at Company B's main data center. Which of the following actions should the CIO take first?
Suggested Answer: B
Community votes
No votes yet
Question 7 of 408
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords.
The company has the following employee password policy:
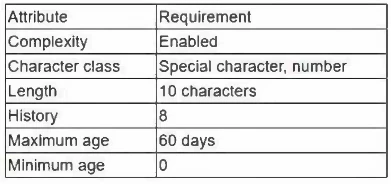
Which of the following should be implemented to best address the password reuse issue? (Choose two.)
The company has the following employee password policy:

Which of the following should be implemented to best address the password reuse issue? (Choose two.)
Suggested Answer: A, B
Community votes
No votes yet
Question 8 of 408
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
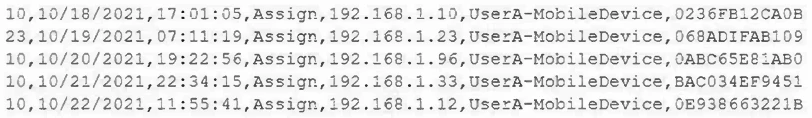
Which of the following mobile configuration settings is the mobile administrator verifying?

Which of the following mobile configuration settings is the mobile administrator verifying?
Suggested Answer: D
Community votes
No votes yet
Question 9 of 408
A security analyst is investigating a possible insider threat incident that involves the use of an unauthorized USB from a shared account to exfiltrate data. The event did not create an alert. The analyst has confirmed the USB hardware ID is not on the device allow list, but has not yet confirmed the owner of the USB device. Which of the following actions should the analyst take next?
Suggested Answer: B
Community votes
No votes yet
Question 10 of 408
Which of the following security features do email signatures provide?
Suggested Answer: A
Community votes
No votes yet