Question 6 of 59
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should the API authentication be implemented?
Suggested Answer: B
Community votes
No votes yet
Question 7 of 59
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access services like database or compute on AWS.
The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
Suggested Answer: A
Community votes
No votes yet
Question 8 of 59
Which statement explains the correct position of a PLC within the CPwE architecture?
Suggested Answer: C
Community votes
No votes yet
Question 9 of 59
A sensor reads potentially critical data from an industrial device, but most of the data from the sensor is not critical information and does not change unless a critical event happens.
Which data work flow is appropriate for how the critical and non-critical data is processed?
Which data work flow is appropriate for how the critical and non-critical data is processed?
Suggested Answer: D
Community votes
No votes yet
Question 10 of 59
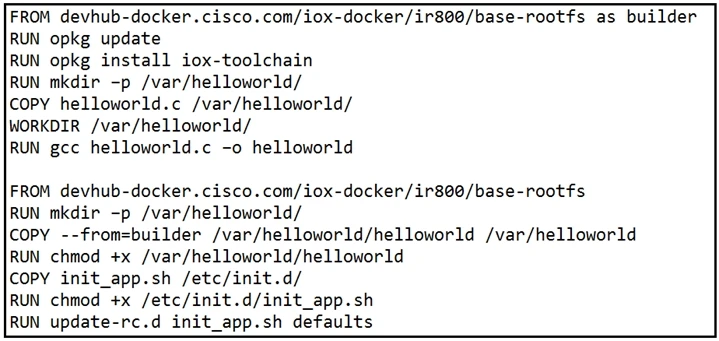
Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)

Refer to the exhibit. When a Docker image is built using this Dockerfile, which two statements are valid on Cisco IOx 1.8 and before? (Choose two.)
Suggested Answer: B, C
Community votes
No votes yet