Question 6 of 61
An agricultural company wants to enhance the cybersecurity posture by implementing a defense-in-depth strategy to protect against polymorphic malware threats. Currently, the company’s security infrastructure relies solely on a stateful traditional edge firewall that does not provide adequate protection against malware variants. Which technology must be added to the company’s security architecture to achieve the goal?
Suggested Answer: D
Community votes
No votes yet
Question 7 of 61
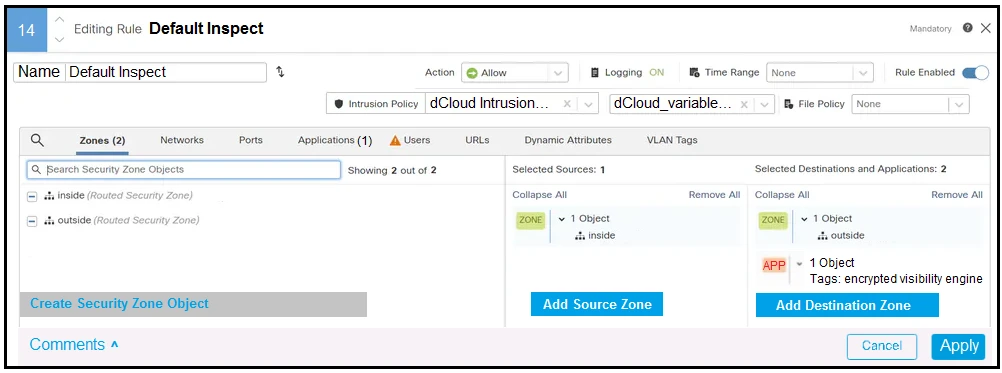
Refer to the exhibit. In addition to SSL decryption, which firewall feature allows malware to be blocked?

Refer to the exhibit. In addition to SSL decryption, which firewall feature allows malware to be blocked?
Suggested Answer: D
Community votes
No votes yet
Question 8 of 61
A construction company recently introduced a BYOD policy, where contractors can bring personal devices and connect to the wireless network. The network engineer configured a Wi-Fi network with a guest splash page to provide internet access only. Although the policy was limited to wireless devices, contractors started bringing devices that needed wired connections without authorization and connecting to the network. The network team suggested shutting down ports where unauthorized devices are connected. Which technology must be implemented to ensure that wired and wireless devices are granted network access only after successful authentication?
Suggested Answer: D
Community votes
No votes yet
Question 9 of 61
After a recent security breach, a financial company is reassessing their overall security posture and strategy to better protect sensitive data and resources. The company already\ deployed on-premises next-generation firewalls at the network edge for each branch location. Security measures must be enhanced at the endpoint level. The goal is to implement a solution that provides additional traffic filtering directly on endpoint devices, thereby offering another layer of defense against potential threats. Which technology must be implemented to meet the requirement?
Suggested Answer: A
Community votes
No votes yet
Question 10 of 61
Network administrators at a medical facility cannot log in to network devices because of excessive resource consumption and high CPU utilization. The situation has led to delays in routine maintenance and troubleshooting, which affects overall network performance. An engineer must optimize the handling of traffic to reduce the impact and maintain consistent access and operational efficiency. Which approach must be implemented to meet the requirement?
Suggested Answer: A
Community votes
No votes yet