Question 6 of 756
Which is the purpose of the Cisco NAC Profiler?
Correct Answer: A
Question 7 of 756
Cisco Identity-Based Networking Services relies heavily on the 802.1X protocol. Which other authentication solution is used hand-in-hand with 802.1X to authenticate users for network access?
Correct Answer: A
Question 8 of 756
Which protocol is used for voice bearer traffic?
Correct Answer: B
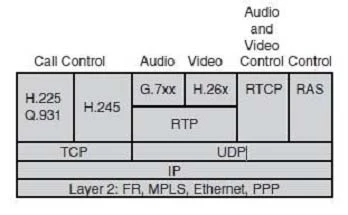
VoIP Control and Transport Protocols
A number of different protocols are used in a VoIP environment for call control, device provisioning, and addressing.
Figure 14-15 shows those protocols focused on VoIP control and transport.
 B
B
A number of different protocols are used in a VoIP environment for call control, device provisioning, and addressing.
Figure 14-15 shows those protocols focused on VoIP control and transport.
 B
BQuestion 9 of 756
Which protocol is used to reserve bandwidth for the transport of a particular application data flow across the network?
Correct Answer: C
Question 10 of 756
Which two features are supported by single wireless controller deployments? (Choose two.)
Correct Answer: A, B