Which of the following honeypots provides an attacker access to the real operating system without any restriction and collects a vast amount of information about the attacker?
A high-interaction honeypot provides an attacker access to the real operating system without any restriction, thus collecting a vast amount of information about the attacker. This type of honeypot is useful for detailed and comprehensive data gathering, including the attacker's behaviors, tools, and communication methods. Unlike low or medium-interaction honeypots, which offer limited interaction and do not provide full access to the underlying operating system, high-interaction honeypots go even further by allowing full OS access, increasing the fidelity and quantity of captured data.
Which of the following representatives of the incident response team takes forensic backups of systems that are the focus of an incident?
The technical representative is responsible for taking forensic backups of systems that are the focus of an incident. This role involves creating copies of data from the systems in a manner that preserves the integrity of the information, ensuring it can be used for further analysis or legal purposes if necessary. The technical representative has the specialized knowledge and skills to manage the technical aspects of back-ups, including understanding and preserving the configuration of the network and target system.
Which of the following refers to the exploitation of a valid computer session to gain unauthorized access to information or services in a computer system?
Session hijacking refers to the exploitation of a valid computer session to gain unauthorized access to information or services in a computer system. This involves taking over an active session by stealing the session ID (such as a cookie) and using it to authenticate as the victim, thereby gaining unauthorized access.
DRAG DROP -
George works as a Network Administrator for Blue Soft Inc. The company uses Windows Vista operating system. The network of the company is continuously connected to the Internet. What will George use to protect the network of the company from intrusion?
Select and Place:
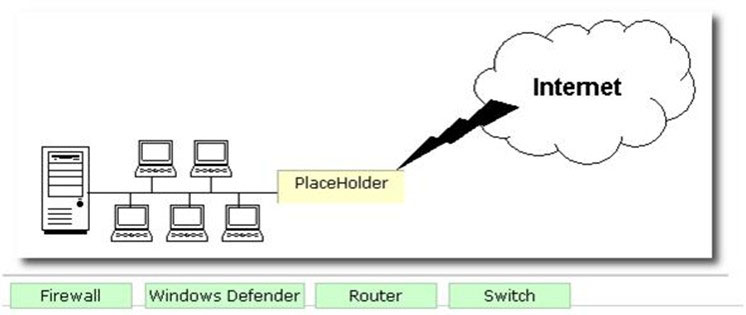
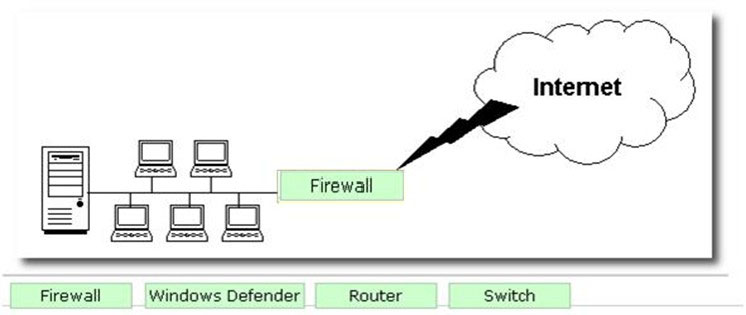
A firewall is a set of related programs configured to protect private networks connected to the Internet from intrusion. It is used to regulate the network traffic between different computer networks. It permits or denies the transmission of a network packet to its destination based on a set of rules. A firewall is often installed on a separate computer so that an incoming packet does not get into the network directly.
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?
The Link Layer of the TCP/IP model is responsible for handling protocols used to transmit data over a physical link and operates on the level of hardware. This layer is used to move packets between the Internet Layer interfaces of two different hosts on the same link. It is concerned with aspects such as MAC addresses, network card drivers, and switches, ensuring that data can travel over the local network or the same physical link. Other layers like Internet, Transport, and Application Layer are responsible for broader network communication tasks and do not handle direct packet movement between devices on the same link.