G.
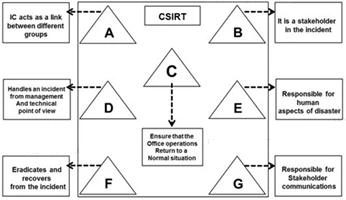

The roles depicted in the flow chart are best matched with the given option D. A is the Incident Manager, acting as a link between groups. B is the Incident Analyst, a stakeholder in the incident. C is Public Relations, ensuring operations return to normal. D is the Administrator, handling incidents from a management and technical viewpoint. E is Human Resources, responsible for human aspects of a disaster. F is the Constituency, eradicating and recovering from incidents. G is the Incident Coordinator, responsible for stakeholder communications. Therefore, the roles align perfectly with option D.
The correct flow of incident recovery steps is: System Restoration involves restoring the affected systems to their operational state. System Validation ensures that the systems have been restored correctly and are functioning as expected. System Operations means putting the validated systems back into normal operations. Finally, System Monitoring is essential to ensure that there are no remaining traces of the incident and that the systems operate smoothly.
A computer risk policy primarily focuses on preventative measures, detection, response, and recovery related to computer security incidents. Procedures to monitor the efficiency of security controls, continuously train employees authorized to access systems, and provide continuing support in case of system interruptions are all inherent aspects of maintaining and managing security risks. However, identifying security funds to hedge risk is more related to financial and business risk management, not directly to the technical or procedural aspects of a computer security risk policy.
Denial of Service Attack is the correct option. This type of attack aims to make a system, network, or application unavailable to its intended users by overwhelming it with a high volume of traffic, thus consuming all available network resources and preventing legitimate use.
The containment step in incident handling and response focuses on limiting the scope and extent of an incident. This involves taking measures to prevent the incident from spreading further and causing more damage, ensuring that it is isolated to a specific area or part of the system while planning and preparing for eradication and recovery.