A company has implemented a requirement to encrypt all the hard drives on its servers as part of a data loss prevention strategy. Which of the following should the company also perform as a data loss prevention method?
If a company has implemented encryption for hard drives on its servers as part of a data loss prevention strategy, one logical additional step would be to ensure all network traffic is encrypted as well. This ensures that data is protected not only at rest but also while in transit, reducing the risk of data interception and loss during communication between devices or over the internet. Encrypting network traffic complements the overall data protection strategy by covering another potential vulnerable point where data could be compromised.
A systems administrator is setting up a server on a LAN that uses an address space that follows the RFC 1918 standard. Which of the following IP addresses should the administrator use to be in compliance with the standard?
According to RFC 1918, certain IP address ranges are reserved for private use and cannot be routed on the public internet. These ranges are: 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255. The IP address 172.16.19.241 falls within the 172.16.0.0 to 172.31.255.255 range, making it a valid private IP address in compliance with RFC 1918.
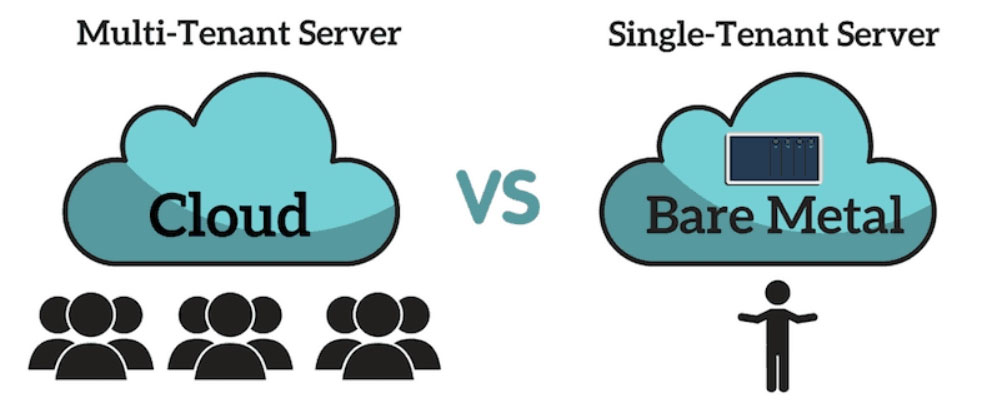
An administrator needs to perform bare-metal maintenance on a server in a remote datacenter. Which of the following should the administrator use to access the server's console?
D
Reference:
https://phoenixnap.com/blog/what-is-bare-metal-server
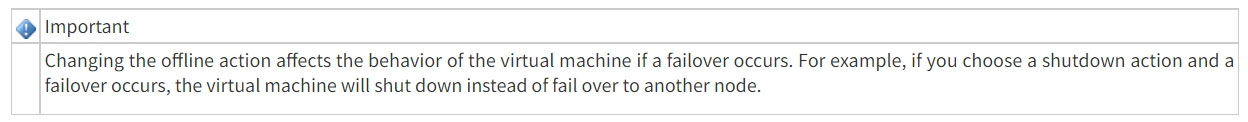
A technician needs to provide a VM with high availability. Which of the following actions should the technician take to complete this task as efficiently as possible?
A
Reference:
https://forsenergy.com/en-us/virtual_help/html/1325909c-5878-4674-a152-3fd3d4e8e3c6.htm
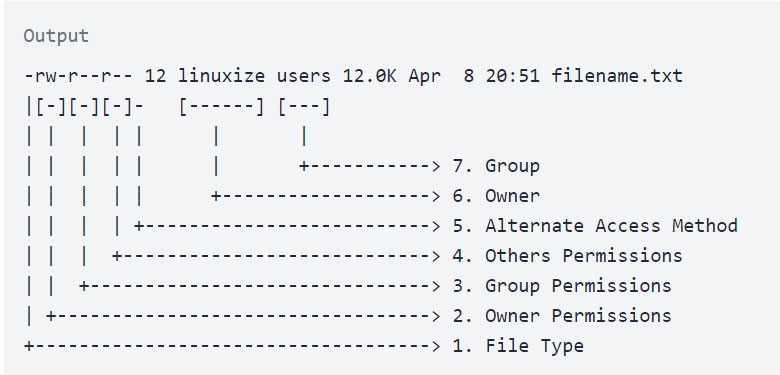
A server administrator receives a report that Ann, a new user, is unable to save a file to her home directory on a server. The administrator checks Ann's home directory permissions and discovers the following: dr-xr-xr-- /home/Ann
Which of the following commands should the administrator use to resolve the issue without granting unnecessary permissions?
D
Reference:
https://linuxize.com/post/what-does-chmod-777-mean/